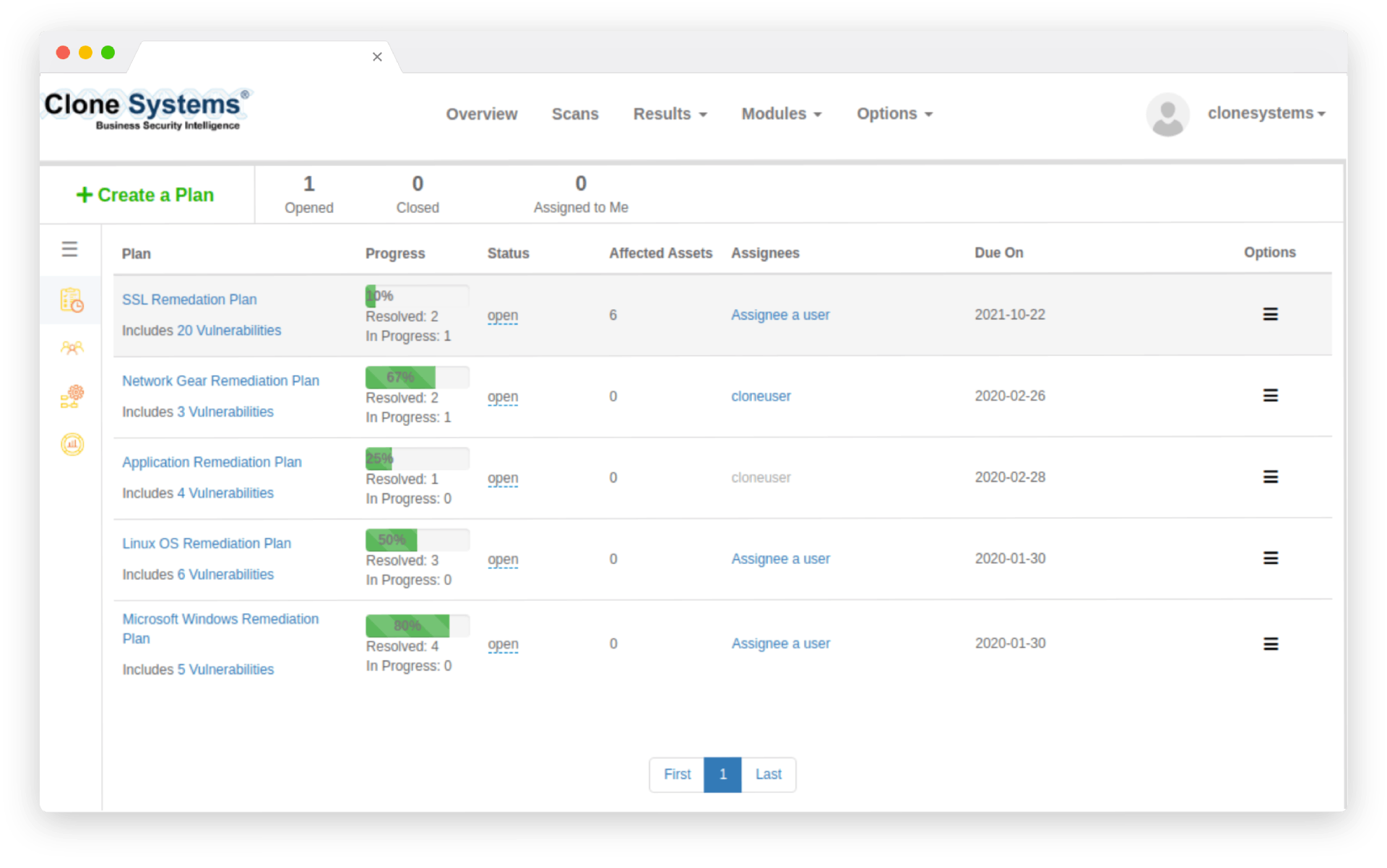
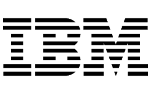Vulnerability Remediation Module
Vulnerability Remediation helps you remediate faster and more efficiently with risk prioritization
Inclusive with our Portal

Vulnerability Remediation Module
Vulnerability Remediation helps you remediate faster and more efficiently with risk prioritization
Inclusive with Clone Systems Portal
Customers Around the World
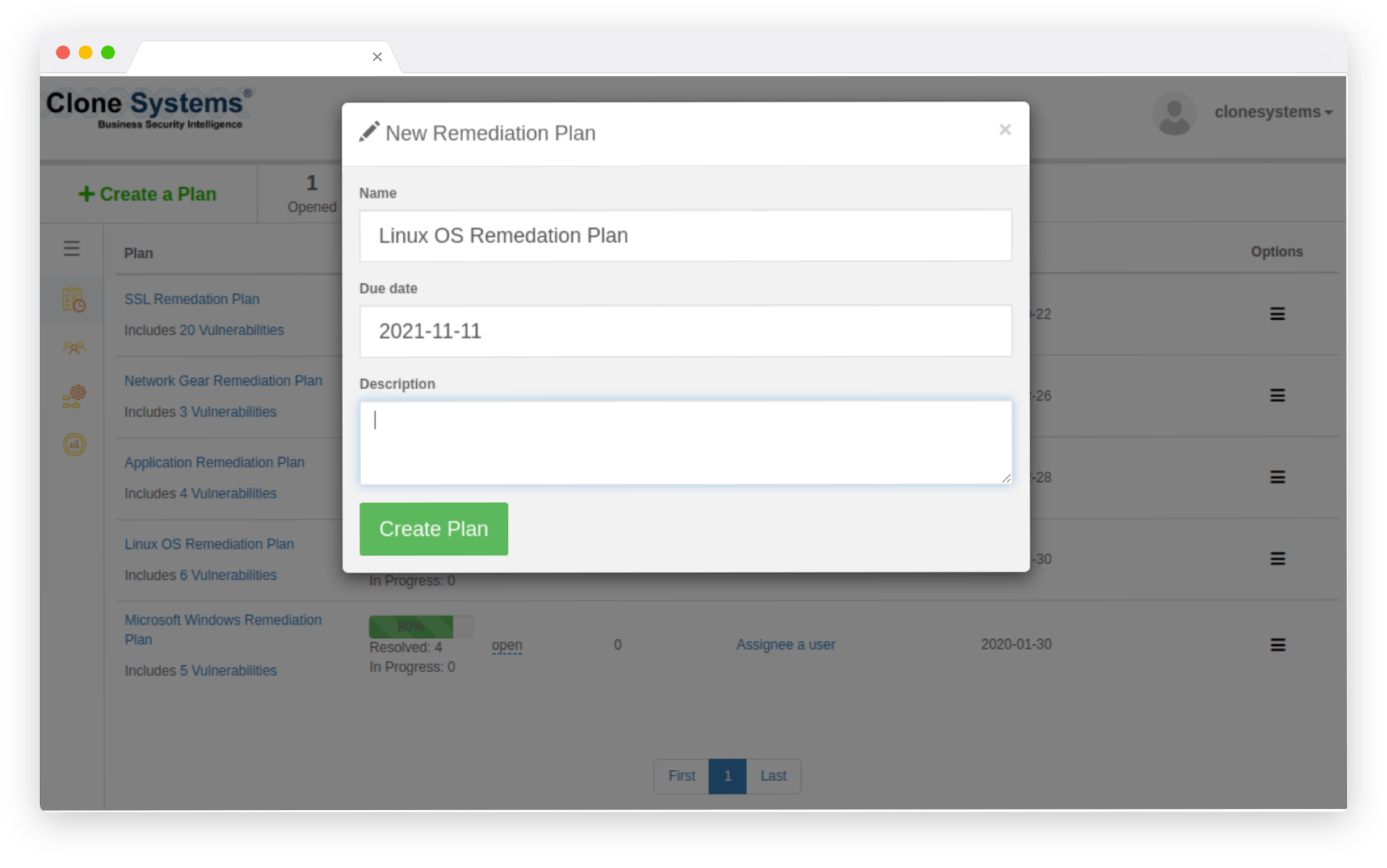
efficiently remediation
Remediate your vulnerabilities more efficiently
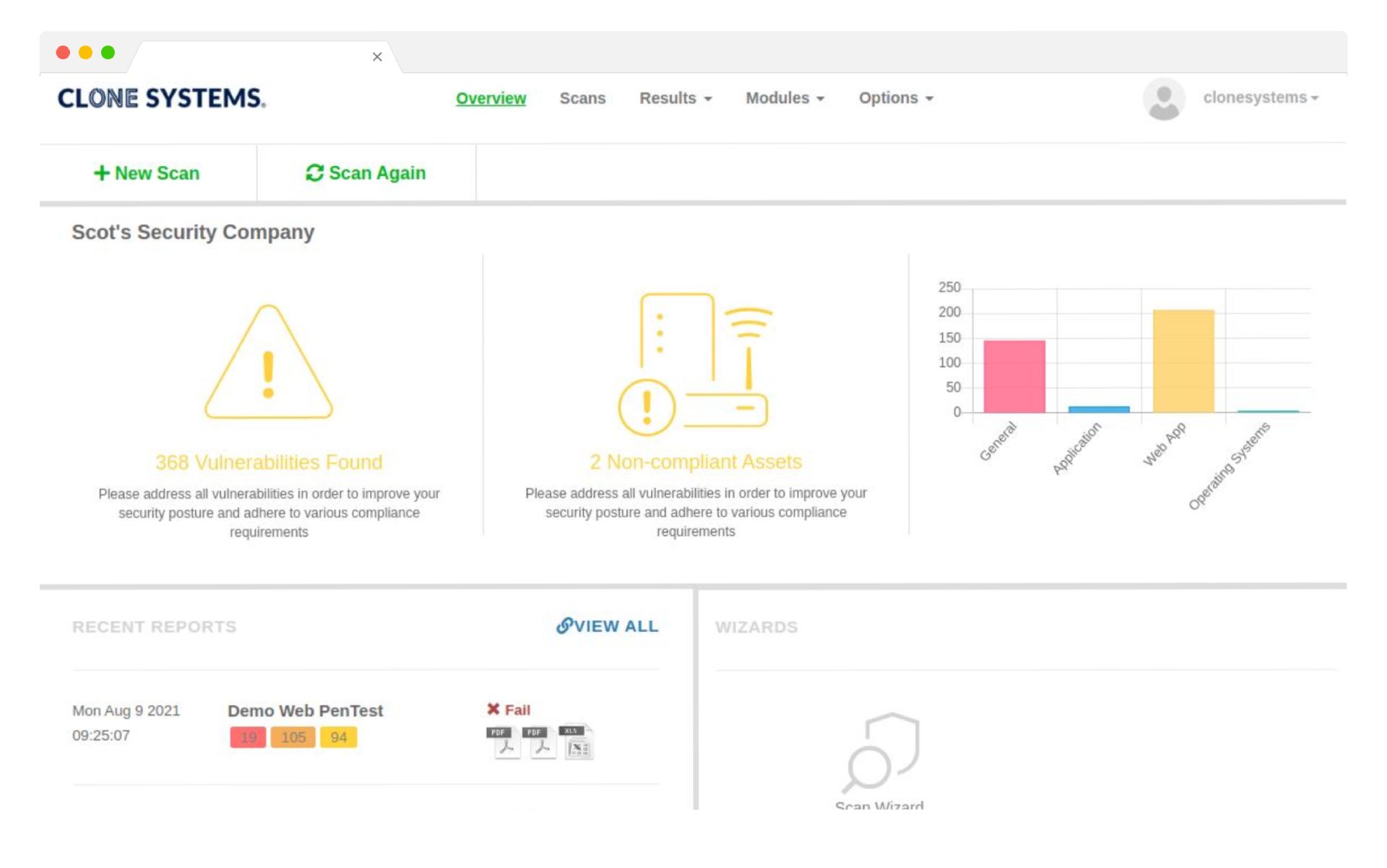
Determine which vulnerabilities pose the highest risk and which can be delegated. Then, filter and sort your vulnerabilities according to the data points that matter to you to reduce noise and ensure your business is protected. Determine the level of risk and prioritize remediation efforts in a multi-vendor environment.
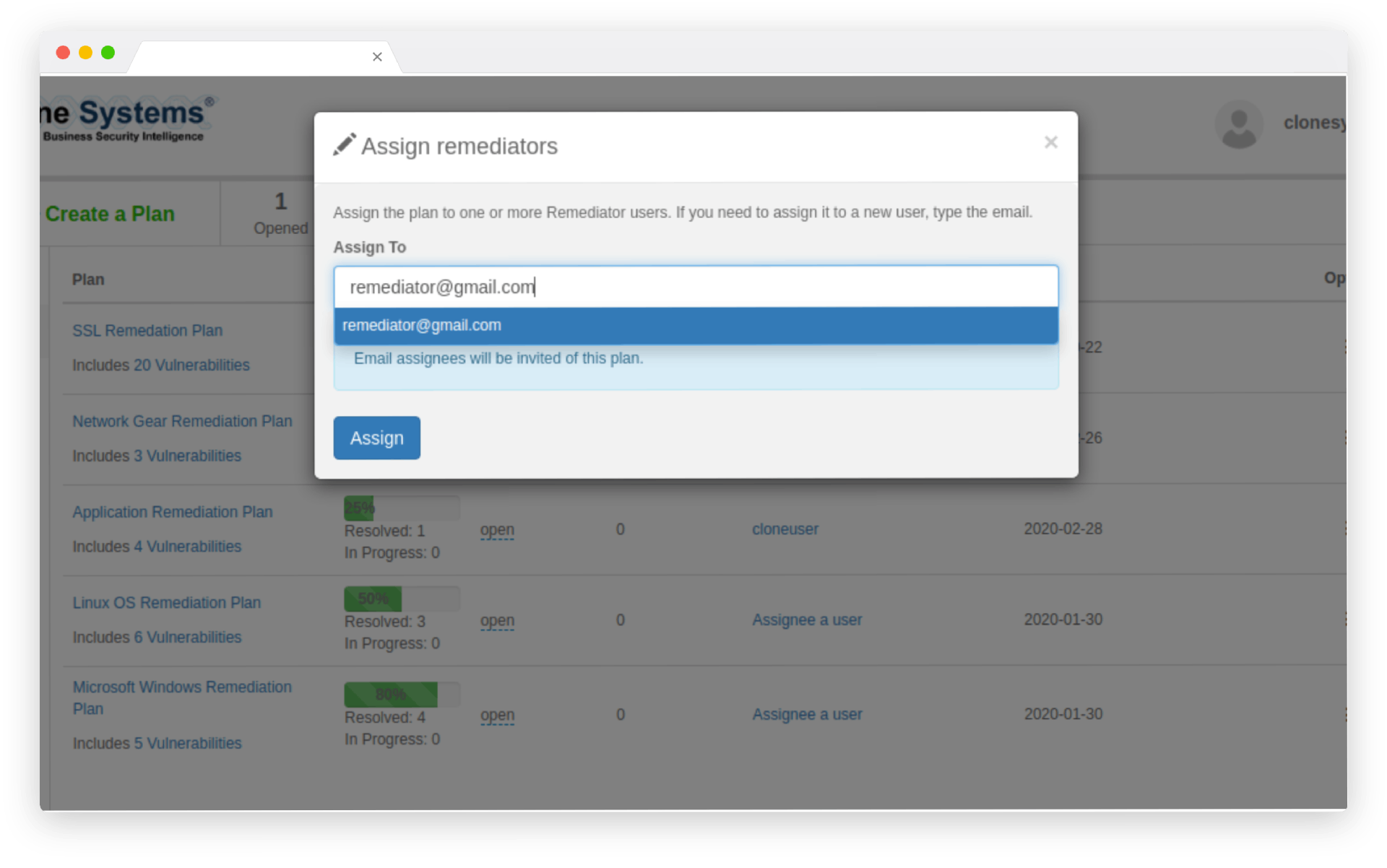
24×7 monitoring
Assign and triage vulnerabilities and hosts
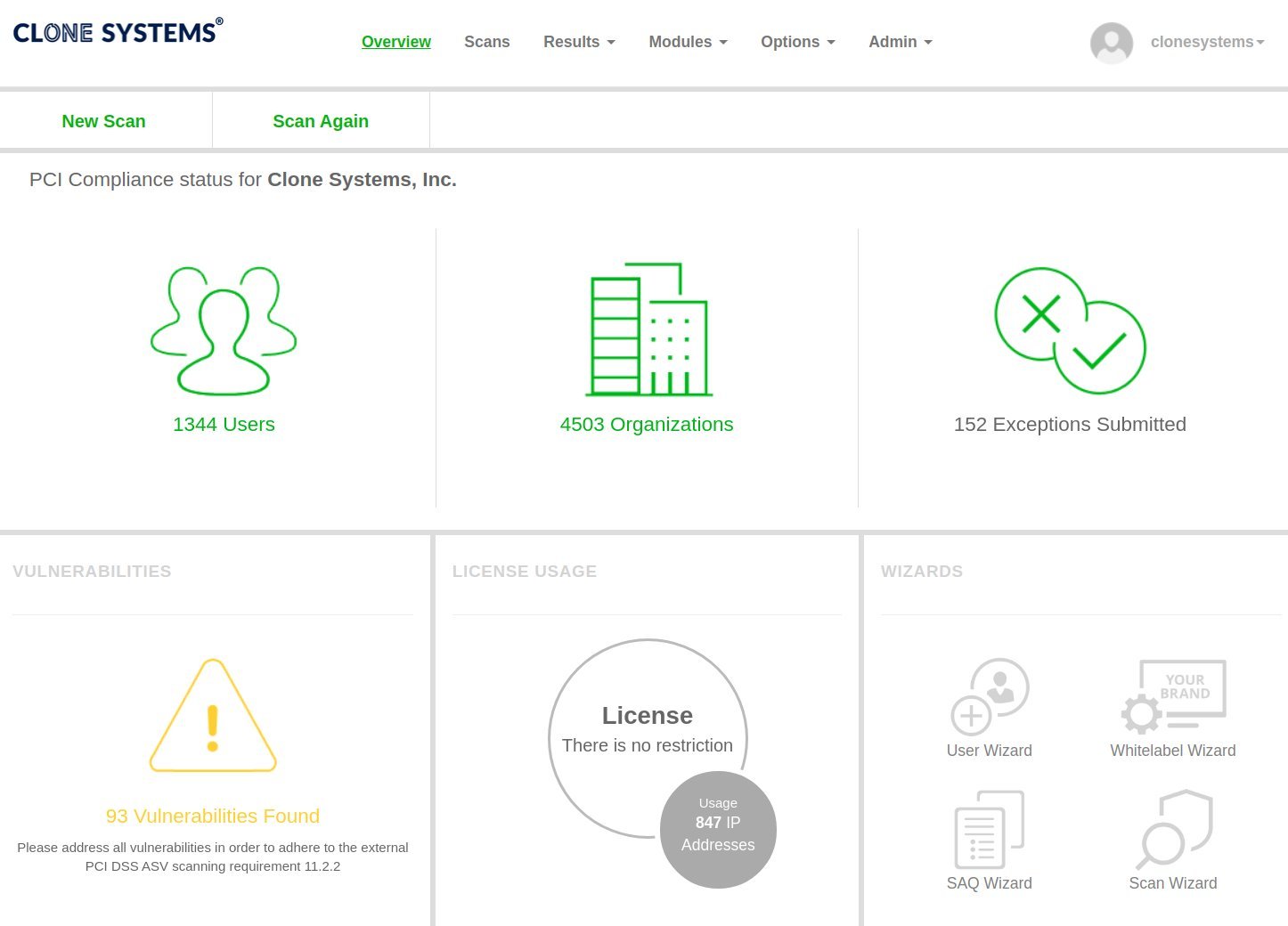
Monitor your company’s risk posture in real-time and see which actions will significantly impact lowering your risk score. Then, create rules for automated triage based on your business intelligence.
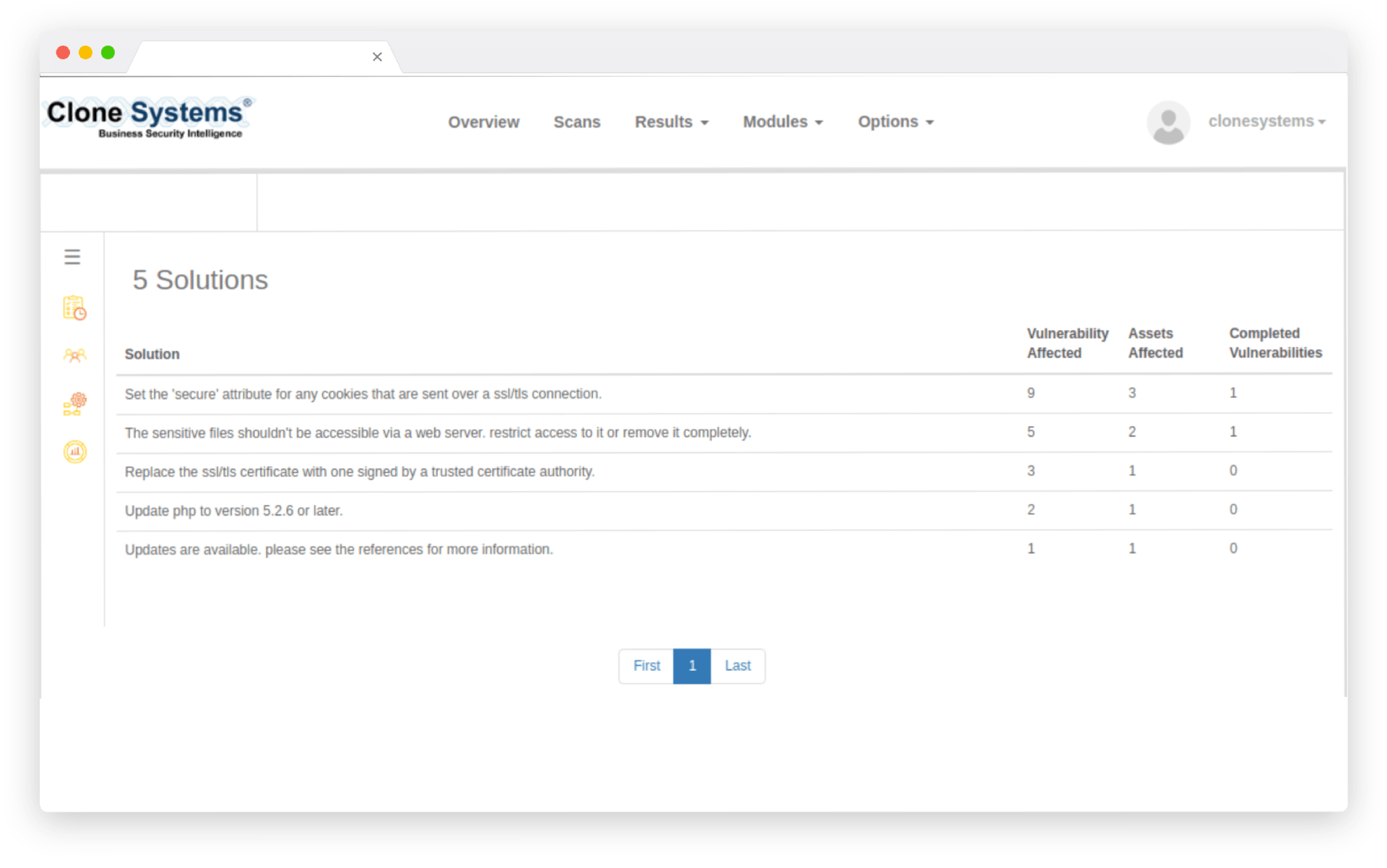
monitor vulnerabilities
Monitor existing vulnerability remediation progress
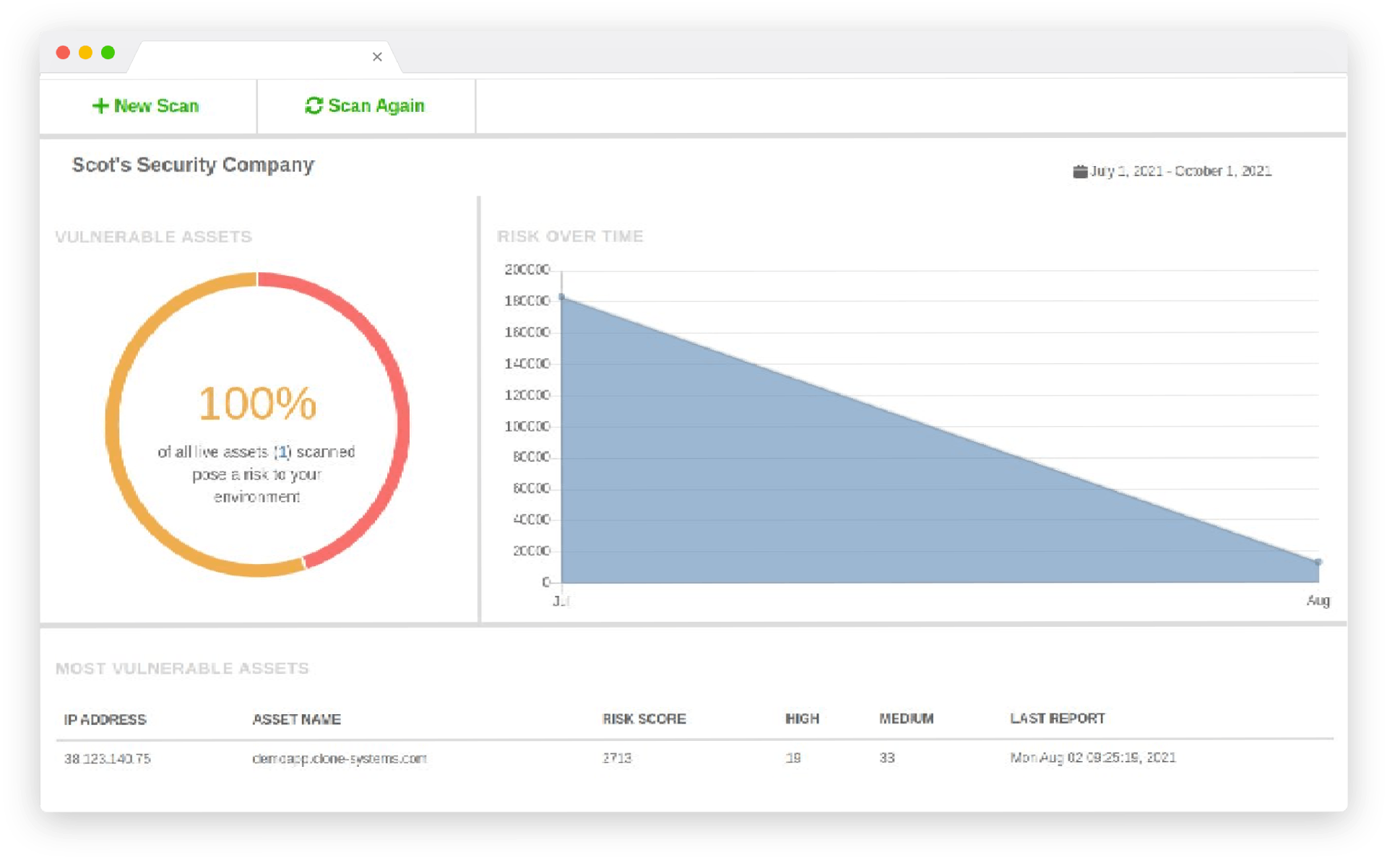
Monitor key performance indicators (KPIs) and service level agreements (SLAs) and optimize your program’s efficiency with a complete audit trail of all your vulnerabilities. Determine which vulnerabilities pose the highest risk and which can be delegated.
EFFICIENTLY REMEDIATION
Remediate your vulnerabilities more efficiently
Determine which vulnerabilities pose the highest risk and which can be delegated. Then, filter and sort your vulnerabilities according to the data points that matter to you to reduce noise and ensure your business is protected. Determine the level of risk and prioritize remediation efforts in a multi-vendor environment.
24×7 MONITORING
Assign and triage vulnerabilities and hosts
Monitor your company’s risk posture in real-time and see which actions will significantly impact lowering your risk score. Then, create rules for automated triage based on your business intelligence.
MONITOR VULNERABILITIES
Monitor existing vulnerability remediation progress
Monitor key performance indicators (KPIs) and service level agreements (SLAs) and optimize your program’s efficiency with a complete audit trail of all your vulnerabilities. Determine which vulnerabilities pose the highest risk and which can be delegated.

What is Vulnerability Remediation?
In any vulnerability management process, vulnerability remediation is a critical step. It refers to the actual steps taken and work completed to mitigate or eliminate threats. Naturally, successful remediation is contingent upon other aspects of vulnerability management, most notably an accurate assessment of potential risks’ threat levels.
To ensure the effectiveness of any cyber security measures implemented as part of your vulnerability remediation efforts and continuously improve your remediation outcomes, you should also evaluate your remediation efforts regularly.
Why is Vulnerability Remediation Important?
Vulnerability remediation that is both effective and efficient has never been more critical. Vulnerabilities are increasing as the volume of data grows, and IT infrastructures become more intricate and complex. Since 2016, the number of Common Vulnerabilities and Exploits (CVEs) discovered in devices, networks, and applications has tripled, according to the National Vulnerability Database. Hackers pounced on the opportunity presented by the increasing number of these flaws.
Vulnerability remediation is critical in this situation. Vulnerabilities must be addressed to reduce the risk of data breaches, denial of service attacks, and business interruptions caused by ransomware or other threats. In today’s environment, minimizing your attack surface and overall exposure is critical, especially since remote work is here to stay, according to Gartner, a fact that makes managing an even more complicated and layered environment even more difficult.