Customers Around the World
Minimize Your Risk
Measure your compliance status against cybersecurity policies and various state and gov laws. Complete trust in the scanning process due to our high-level scanning accuracy. Modern cloud-based scanning technology performs a transparent examination of your network and devices.
Minimize Your Risk
Measure your compliance status against cybersecurity policies and various state and gov laws. Complete trust in the scanning process due to our high-level scanning accuracy. Modern cloud-based scanning technology performs a transparent examination of your network and devices.
External Vulnerability Scanning
Cloud-based scanners continually evaluate the perimeter of your environment. Public, internet-facing vulnerabilities and weaknesses are identified and reported. No software installation or deployment required
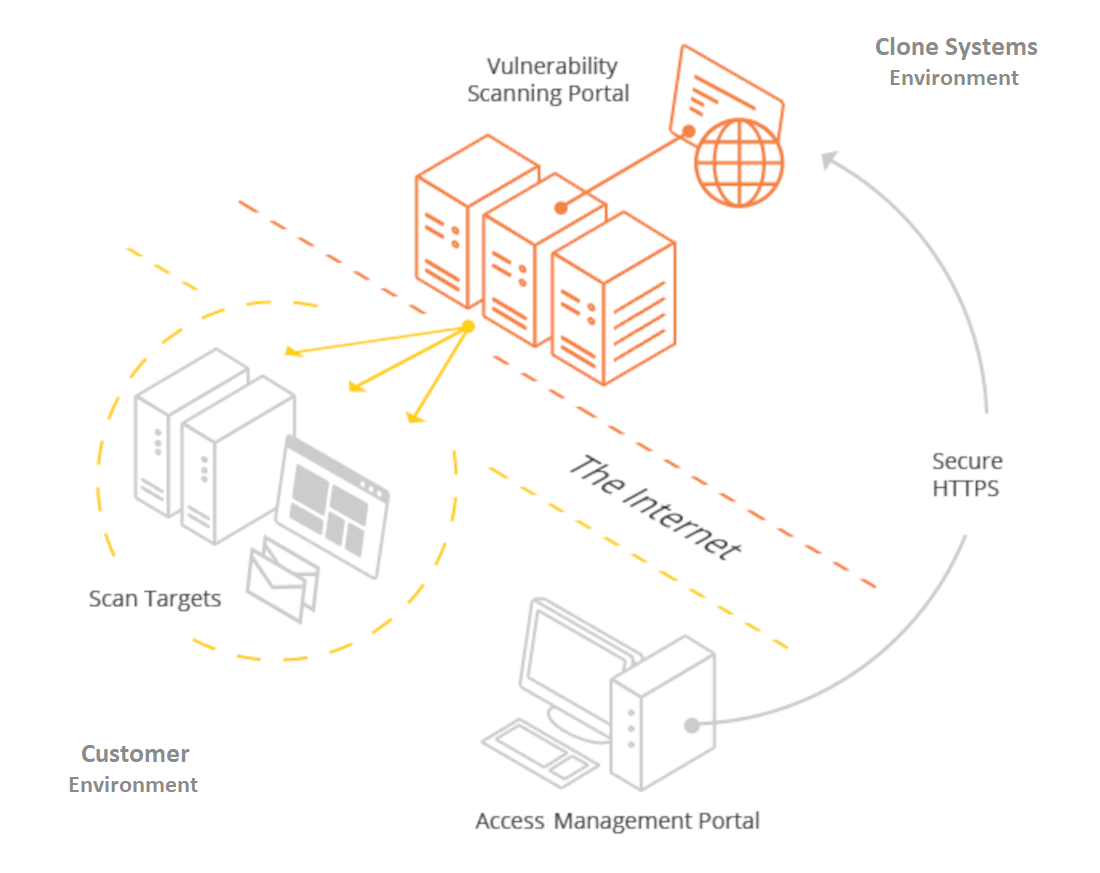

External Vulnerability Scanning
Cloud-based scanners continually evaluate the perimeter of your environment. Public, internet-facing vulnerabilities and weaknesses are identified and reported. No software installation or deployment required.
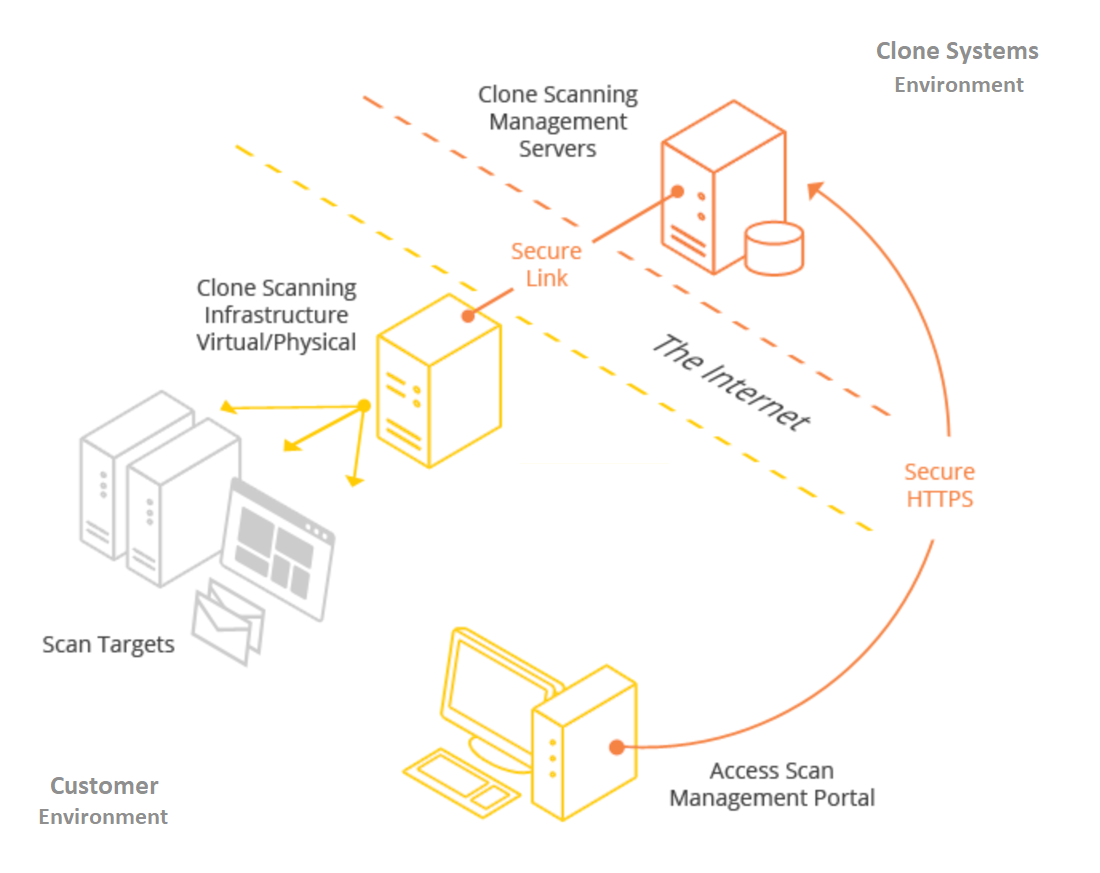
Internal Vulnerability Scanning
Internal vulnerability scanning requires setting up a security scanning server within your network. Physical and virtual options exist. (VMware, VirtualBox, Microsoft Hyper-V, and Citrix XEN, to name a few) Perform full credentialed or partial un-credentialed scans against your assets.

Internal Vulnerability Scanning
Internal vulnerability scanning requires setting up a security scanning server within your network. Physical and virtual options exist. (VMware, VirtualBox, Microsoft Hyper-V, and Citrix XEN, to name a few) Perform full credentialed or partial un-credentialed scans against your assets.
45M+
Vulnerability Checks
Performed Daily
7M+
Vulnerabilities
Uncovered Daily
21K+
Remediations
Performed Weekly
400+
New Signatures
Added Monthly
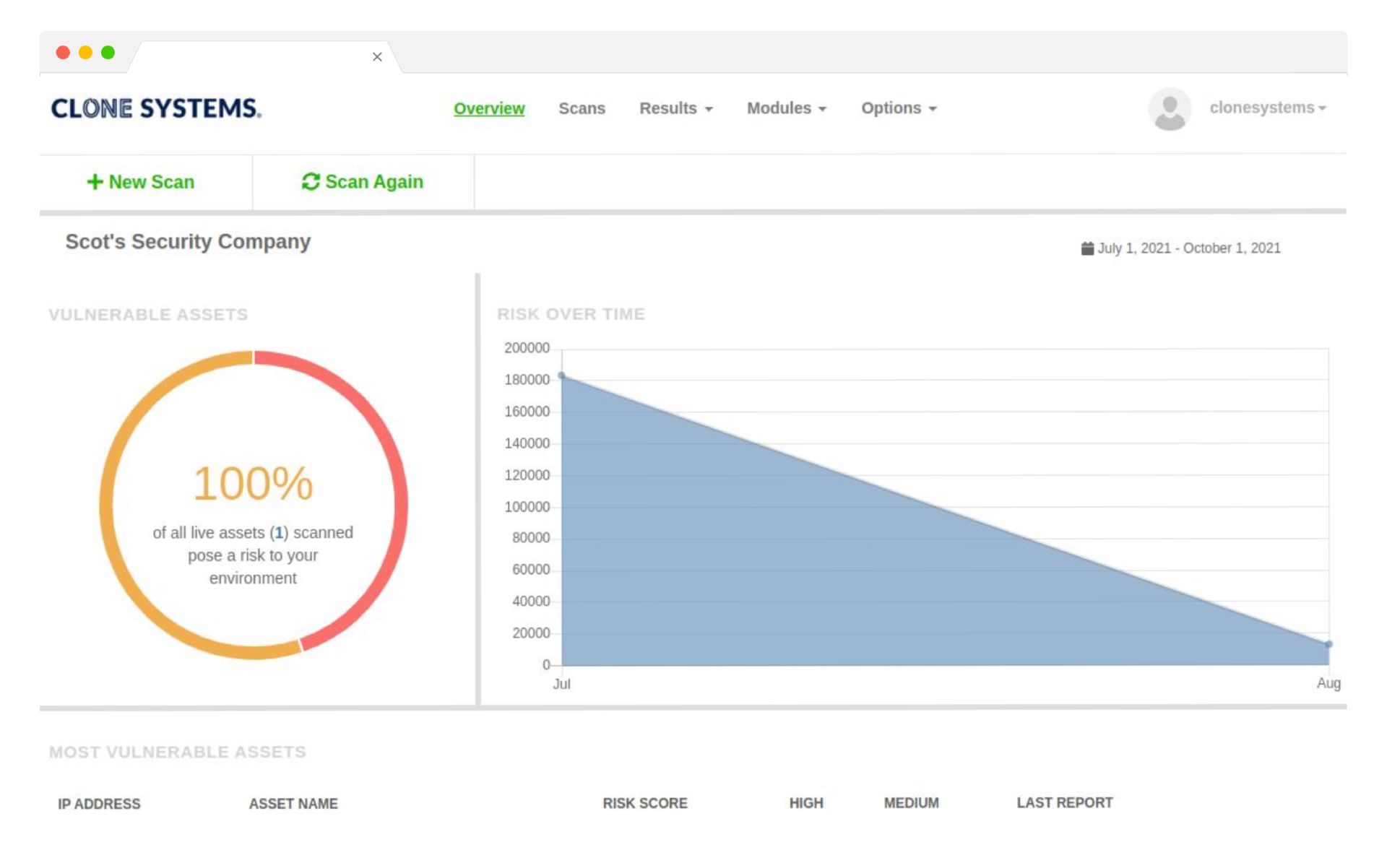
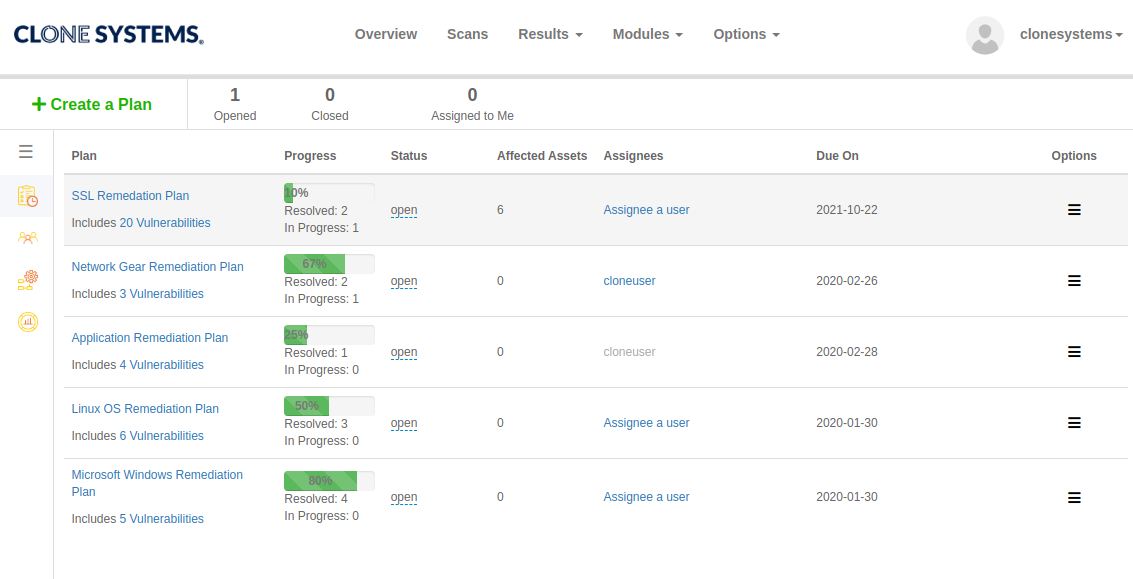
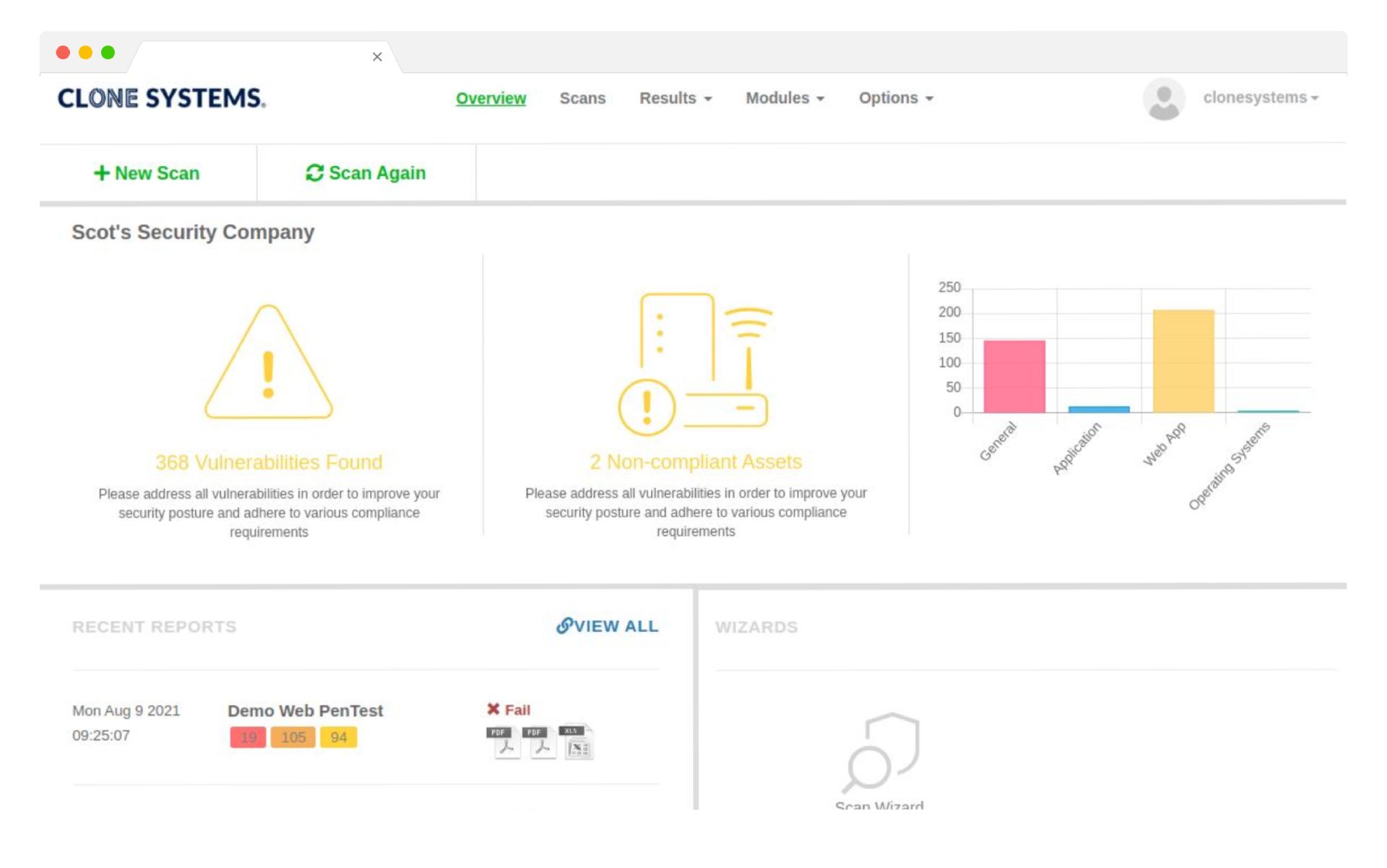
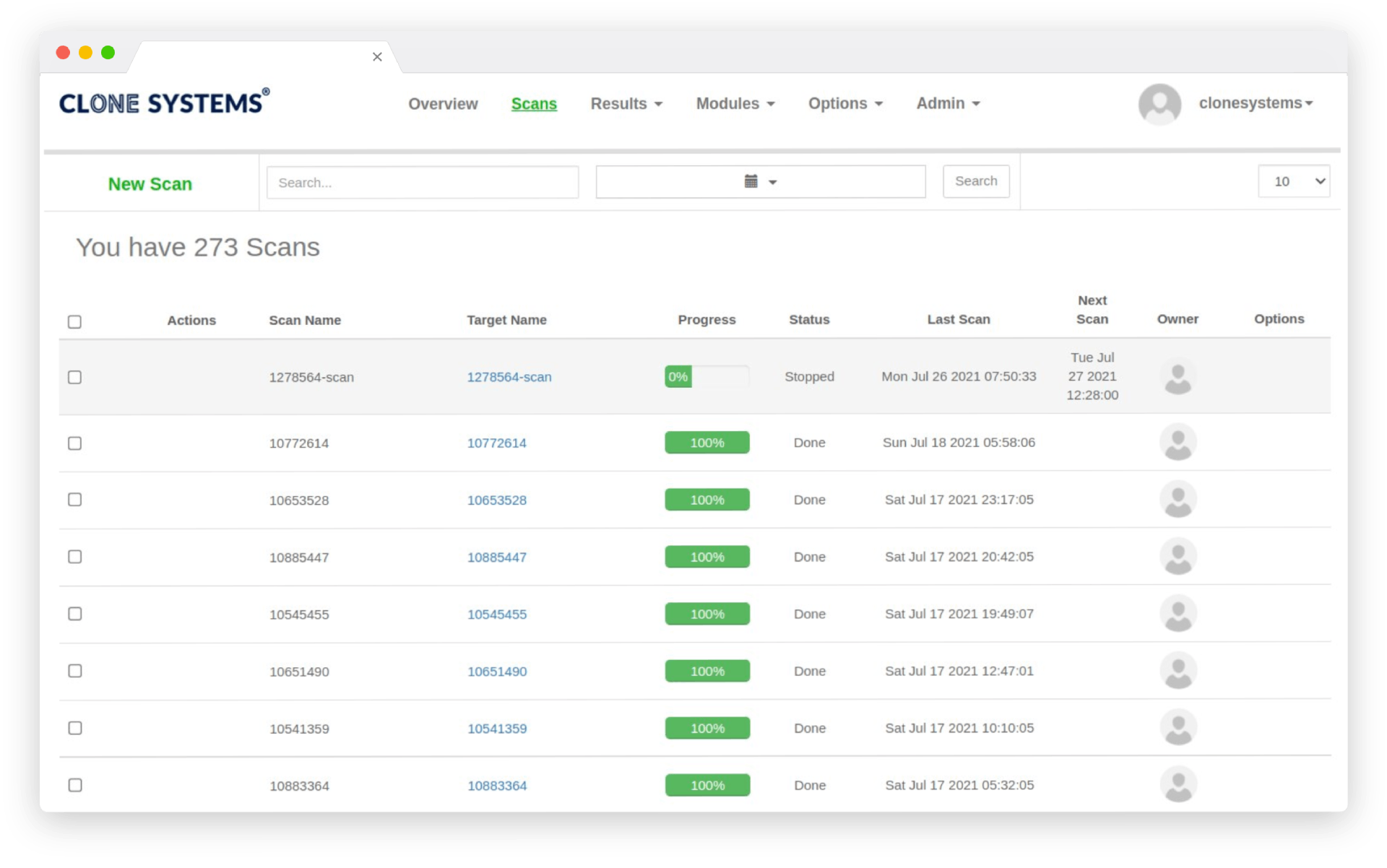
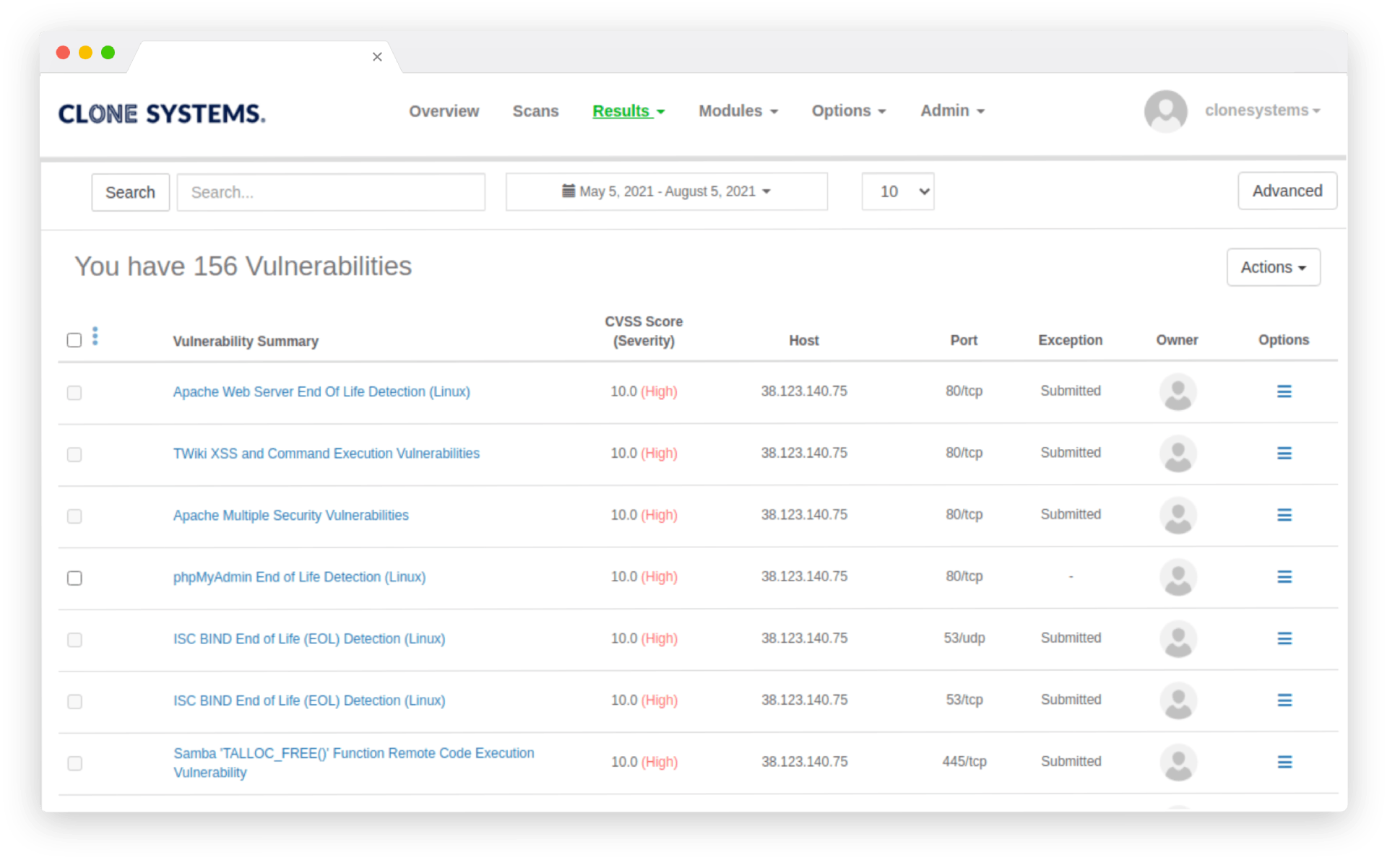
Perform Internal & External Vulnerability scans
Evaluate your infrastructure’s security to identify vulnerabilities and obtain recommendations to improve security.
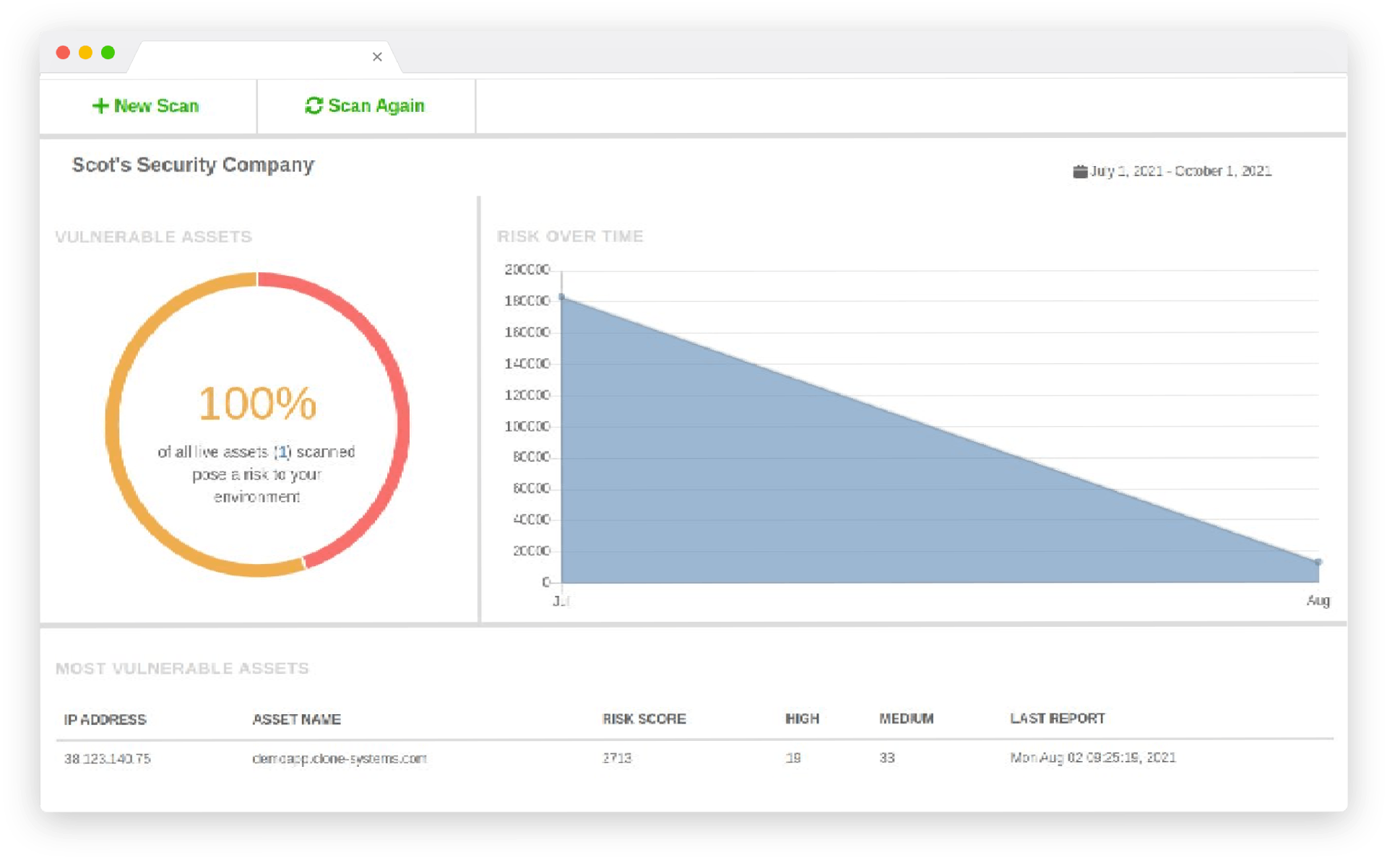

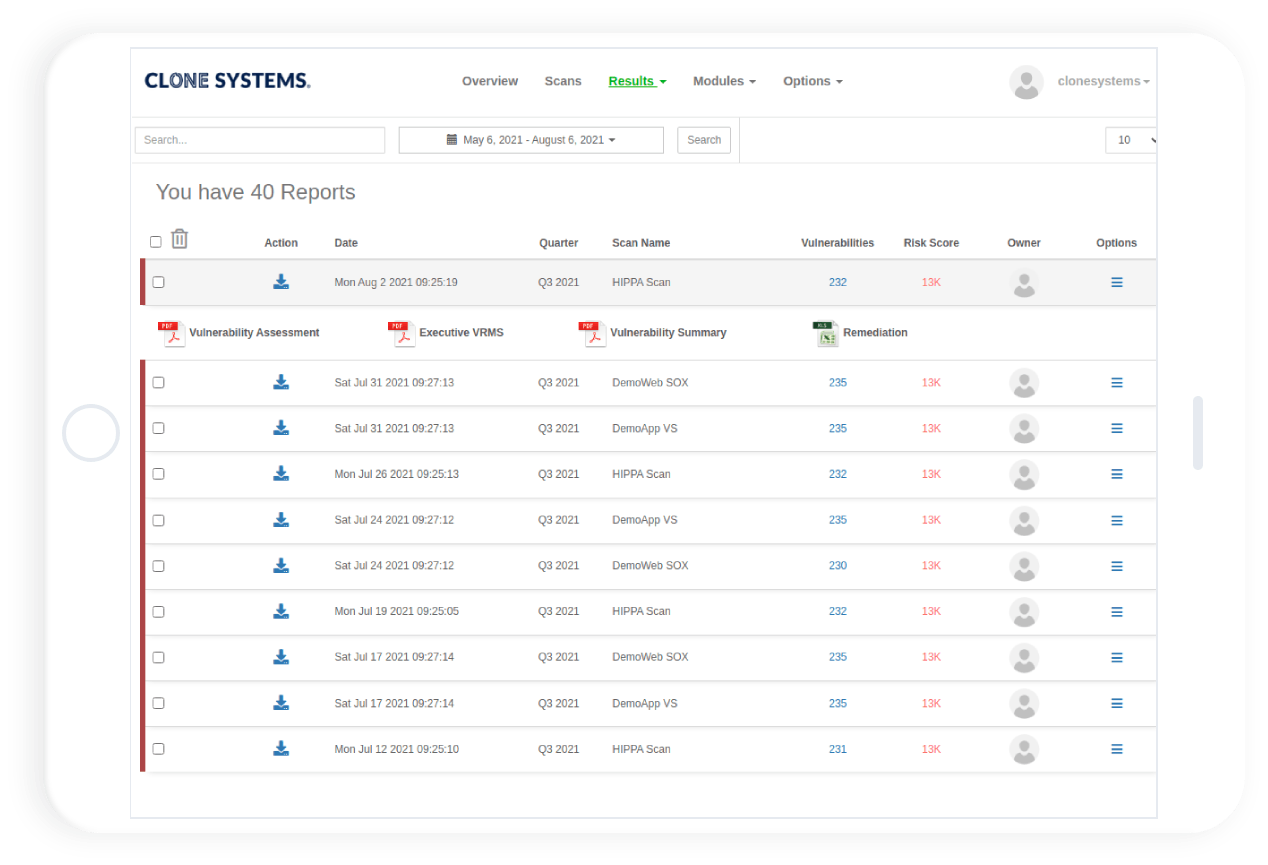
Perform Internal & External Vulnerability scans
Evaluate your infrastructure’s security to identify vulnerabilities and obtain recommendations to improve security.
Easy to use self-managed web-based scanning portal

Perform internal & external vulnerability scans
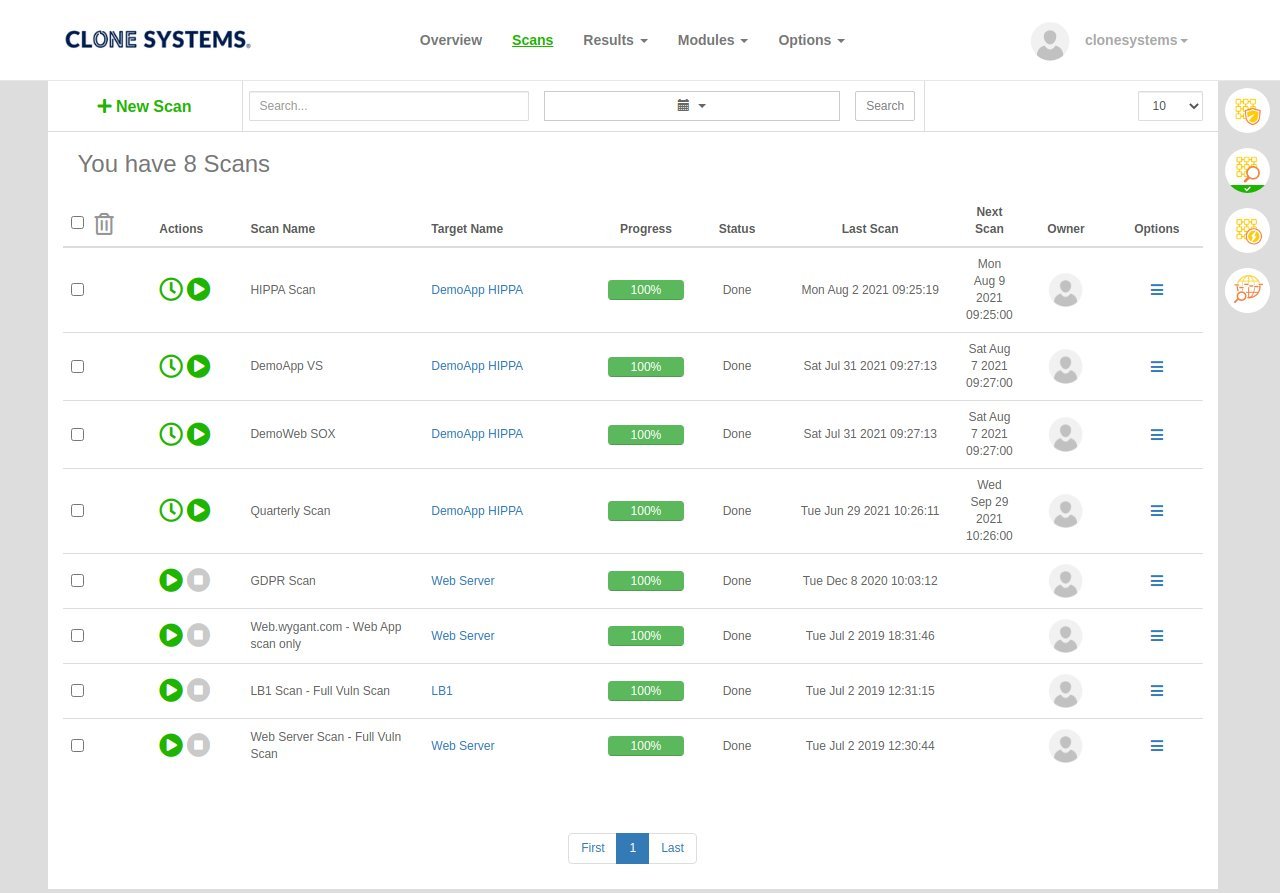
Detailed reports display all risks and threats