SOC as a Service
Security Operation Center (SOC) as a Service is the most cost-effective approach to safeguard your business.
Talk with our experts

SOC as a Service
Security Operation Center (SOC) as a Service is the most cost-effective approach to safeguard your business.
Customers Around the World

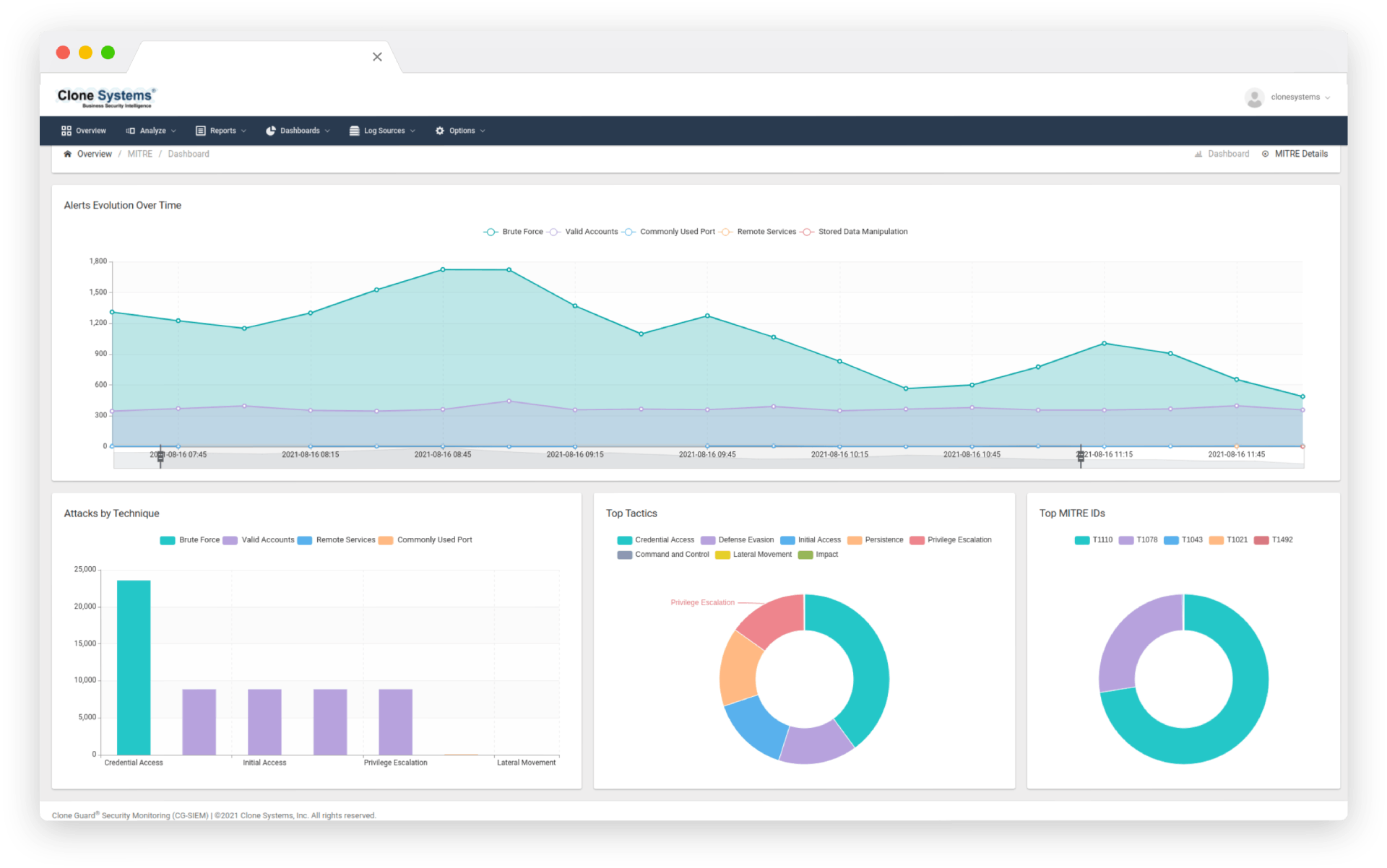
Managed SIEM
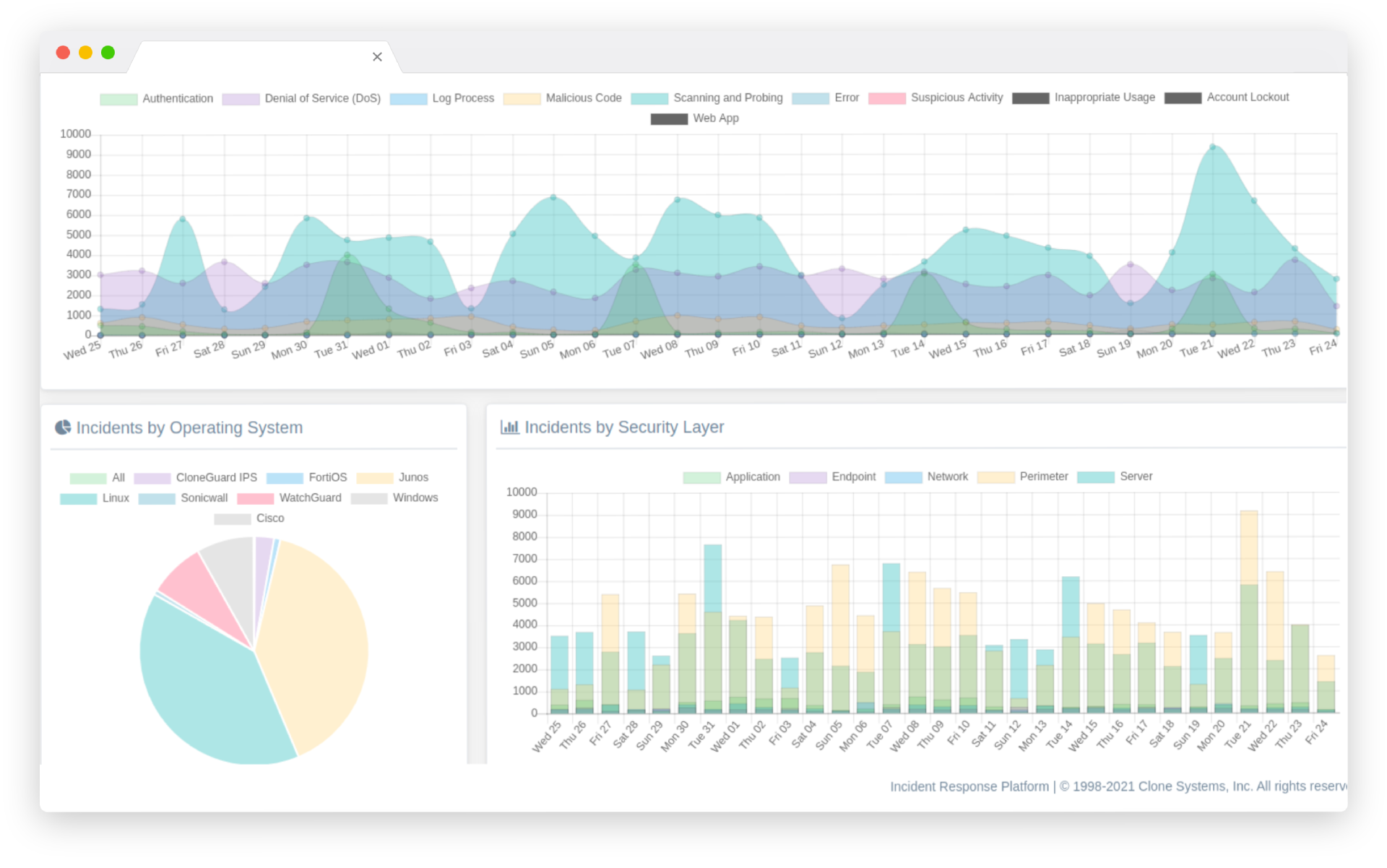
Managed SIEM gives you the power to proactively monitor your organization’s security posture, detect threats in real-time, and respond quickly to potential breaches. With our expert team managing your SIEM solution, you can rest assured that your critical assets are protected 24/7. Our comprehensive reporting and analysis capabilities provide valuable insights into your security environment, allowing you to make informed decisions that enhance your overall security posture. Partner with us today to leverage the benefits of Managed SIEM and stay ahead of emerging threats.

Security Orchestration Automation & Response (SOAR)
Automate your security operations with SOAR – our advanced solution that streamlines your incident response processes, reduces manual tasks, and enables your team to respond to potential threats quickly and effectively. With real-time threat detection and automated incident response, you can minimize the impact of cyber attacks and prevent future incidents. Contact us today to learn how SOAR can enhance your organization’s security posture.

Extended Detection and Response (XDR)
Our XDR solution delivers real-time insights and automated response actions to help you quickly identify and mitigate security incidents. With comprehensive visibility across endpoints, networks, and cloud environments, you can proactively detect and prevent attacks before they cause damage. Boost your security posture and stay ahead of evolving threats with XDR.

Managed Detection and Response (MDR)
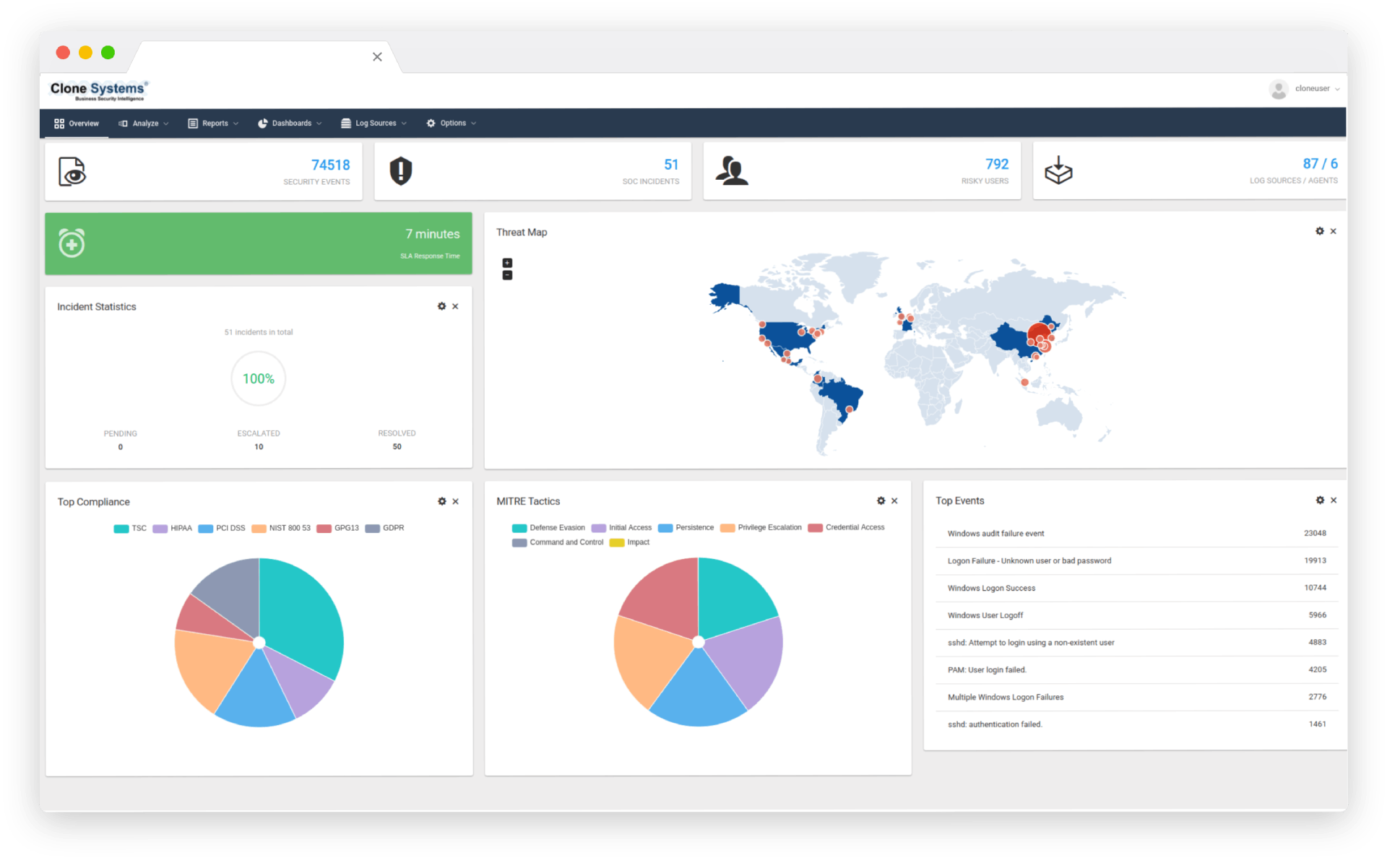
Our expert team proactively monitors your organization’s security environment 24/7, detecting and responding to potential threats in real-time. With our comprehensive reporting and analysis capabilities, you can gain valuable insights into your security posture and make informed decisions that enhance your overall protection. Partner with us today to leverage the benefits of MDR and protect your critical assets from evolving cyber threats.

Endpoint Detection & Response (EDR)
Our EDR solution offers continuous monitoring and rapid response to threats, enabling you to proactively defend against attacks and minimize damage. With detailed forensic analysis and incident response capabilities, our EDR solution empowers you to quickly identify and neutralize threats before they become major incidents. Partner with us today to strengthen your endpoint security and protect your critical assets.

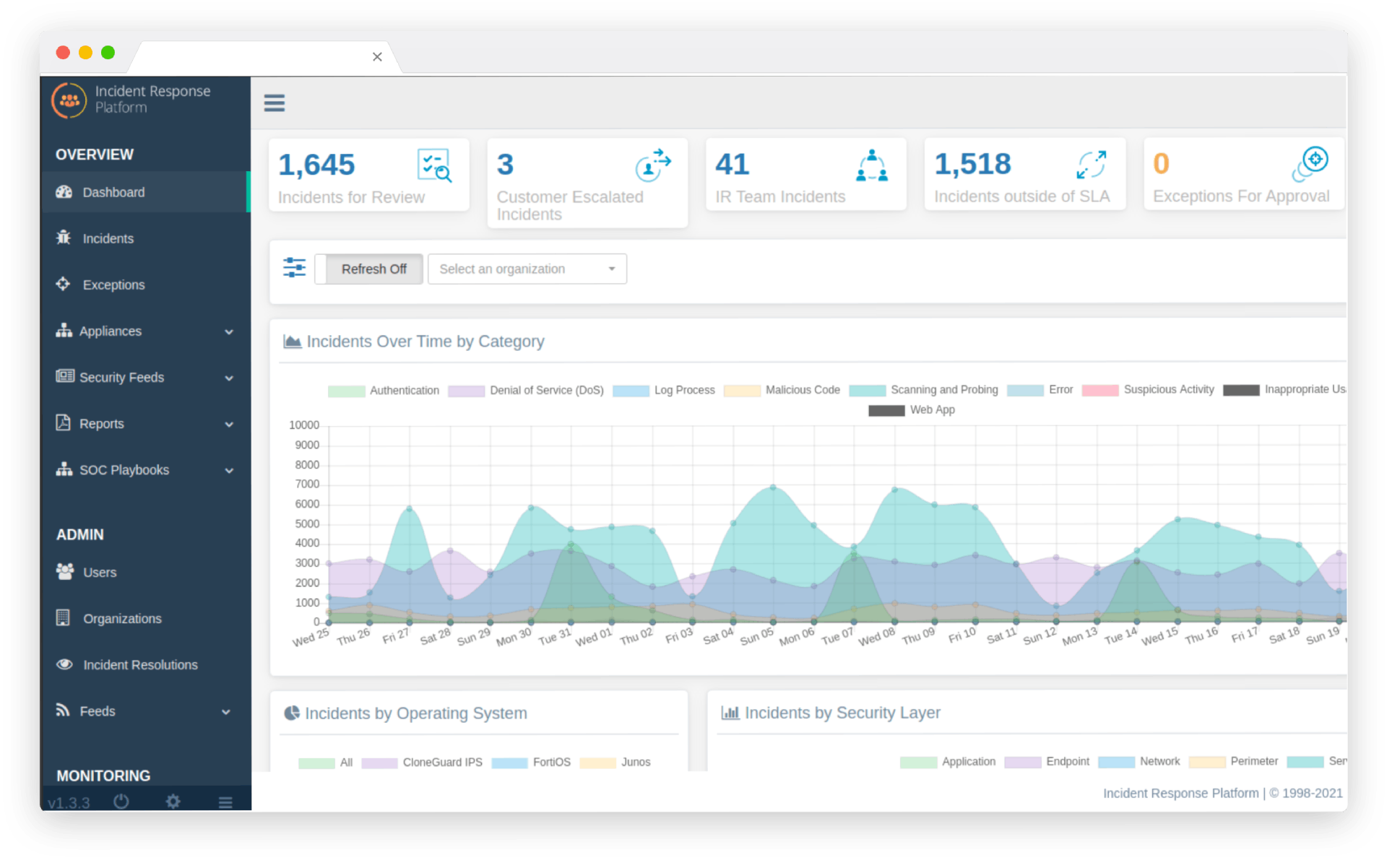
Log Management
Log Management is the backbone of any security strategy, enabling organizations to detect and respond to security threats before they become major incidents. With our Log Management solution, you can quickly identify security incidents, investigate root causes, and take action to remediate them. Our comprehensive reporting and analysis capabilities provide valuable insights into your security environment, allowing you to make informed decisions that enhance your overall security posture.

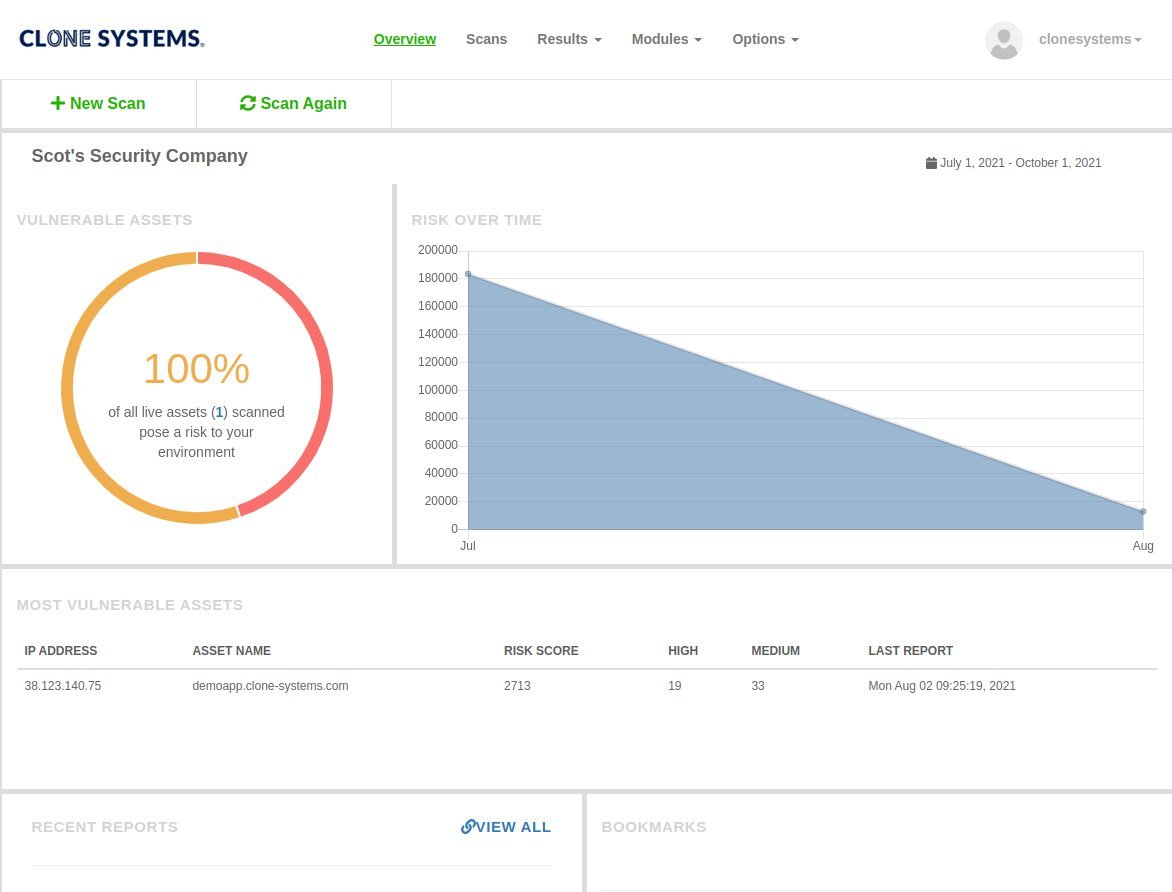
Vulnerability Assessment
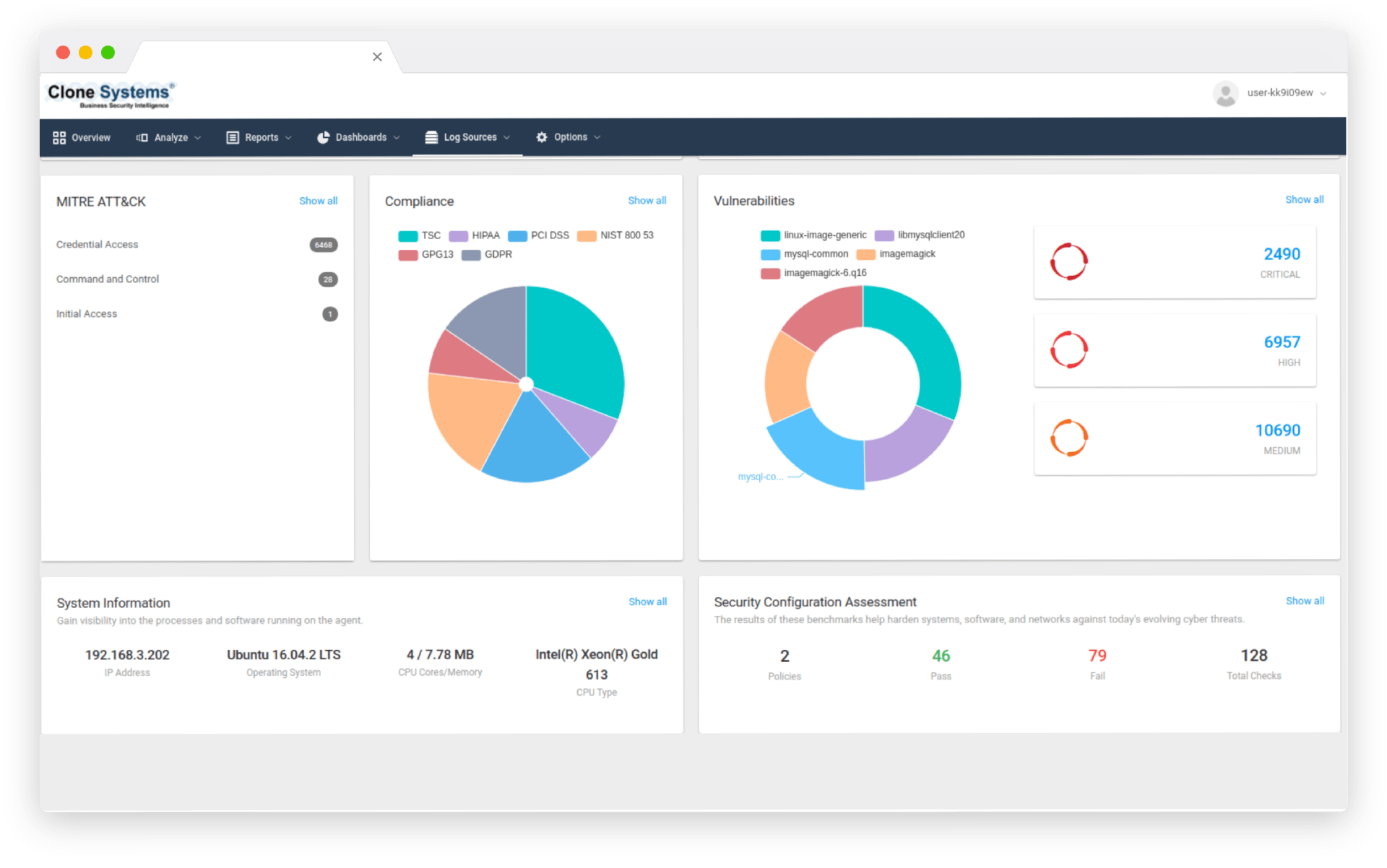
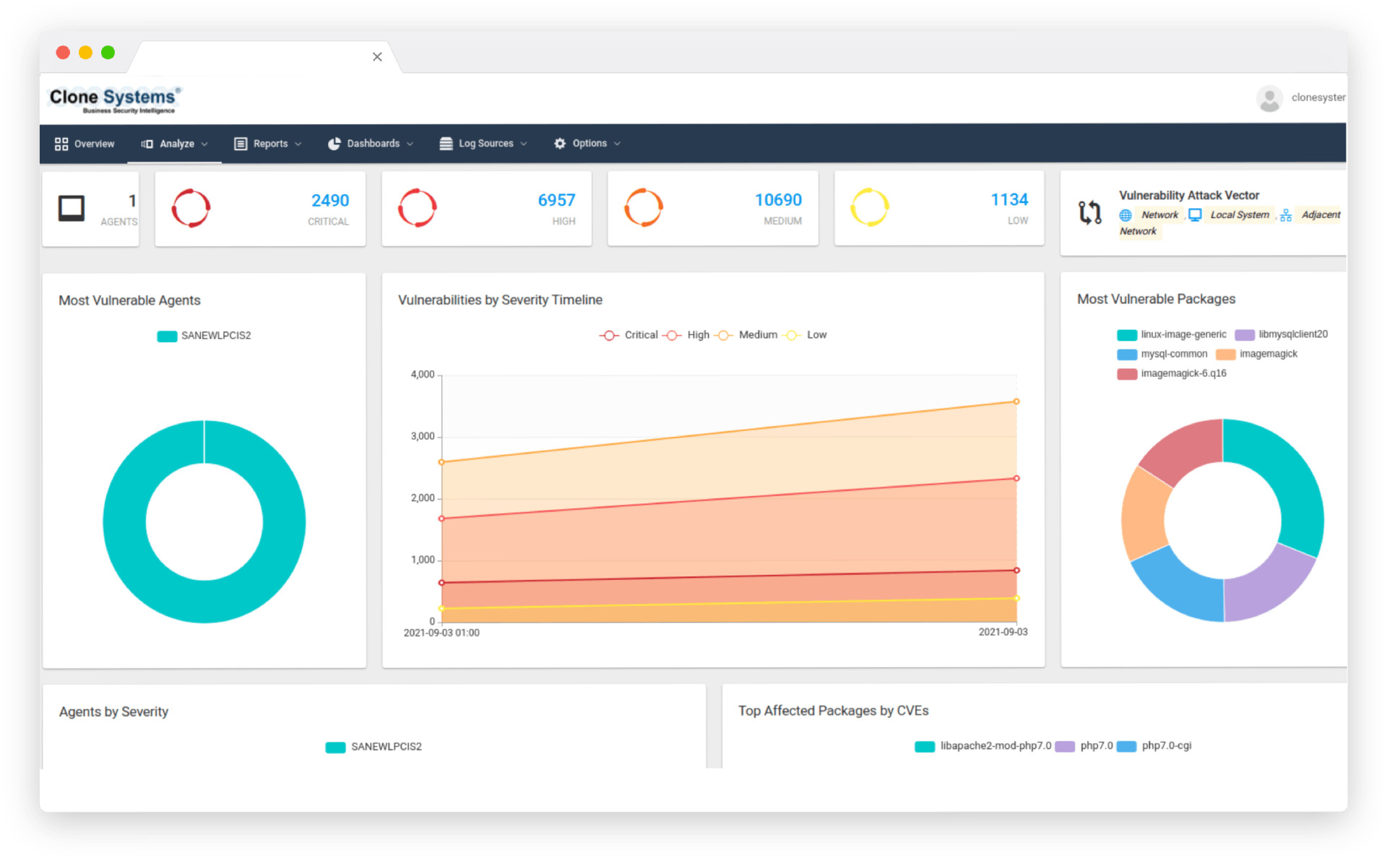
Identify and prioritize vulnerabilities in your infrastructure, applications, and endpoints. Our expert team provides actionable recommendations to remediate identified vulnerabilities, helping you maintain compliance and avoid potential data breaches. Partner with us to gain peace of mind and protect your critical assets from emerging threats.

Managed SIEM
Managed SIEM gives you the power to proactively monitor your organization’s security posture, detect threats in real-time, and respond quickly to potential breaches. With our expert team managing your SIEM solution, you can rest assured that your critical assets are protected 24/7. Our comprehensive reporting and analysis capabilities provide valuable insights into your security environment, allowing you to make informed decisions that enhance your overall security posture. Partner with us today to leverage the benefits of Managed SIEM and stay ahead of emerging threats.

Security Orchestration Automation & Response (SOAR)
Automate your security operations with SOAR – our advanced solution that streamlines your incident response processes, reduces manual tasks, and enables your team to respond to potential threats quickly and effectively. With real-time threat detection and automated incident response, you can minimize the impact of cyber attacks and prevent future incidents. Contact us today to learn how SOAR can enhance your organization’s security posture.

Extended Detection and Response (XDR)
Our XDR solution delivers real-time insights and automated response actions to help you quickly identify and mitigate security incidents. With comprehensive visibility across endpoints, networks, and cloud environments, you can proactively detect and prevent attacks before they cause damage. Boost your security posture and stay ahead of evolving threats with XDR.
Managed Detection and Response (MDR)
Our expert team proactively monitors your organization’s security environment 24/7, detecting and responding to potential threats in real-time. With our comprehensive reporting and analysis capabilities, you can gain valuable insights into your security posture and make informed decisions that enhance your overall protection. Partner with us today to leverage the benefits of MDR and protect your critical assets from evolving cyber threats.
Endpoint Detection & Response (EDR)
Our EDR solution offers continuous monitoring and rapid response to threats, enabling you to proactively defend against attacks and minimize damage. With detailed forensic analysis and incident response capabilities, our EDR solution empowers you to quickly identify and neutralize threats before they become major incidents. Partner with us today to strengthen your endpoint security and protect your critical assets.
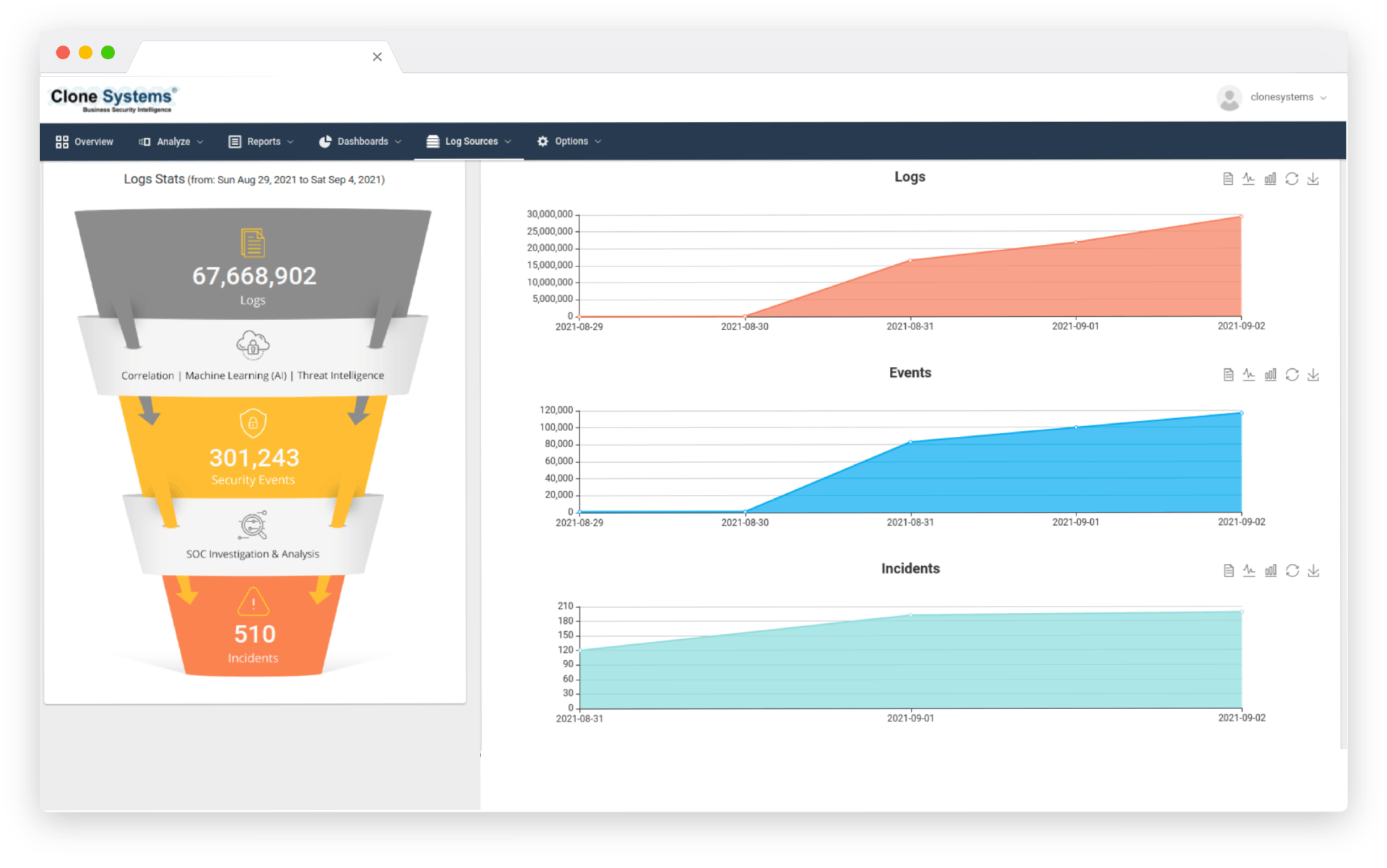
Log Management
Log Management is the backbone of any security strategy, enabling organizations to detect and respond to security threats before they become major incidents. With our Log Management solution, you can quickly identify security incidents, investigate root causes, and take action to remediate them. Our comprehensive reporting and analysis capabilities provide valuable insights into your security environment, allowing you to make informed decisions that enhance your overall security posture.
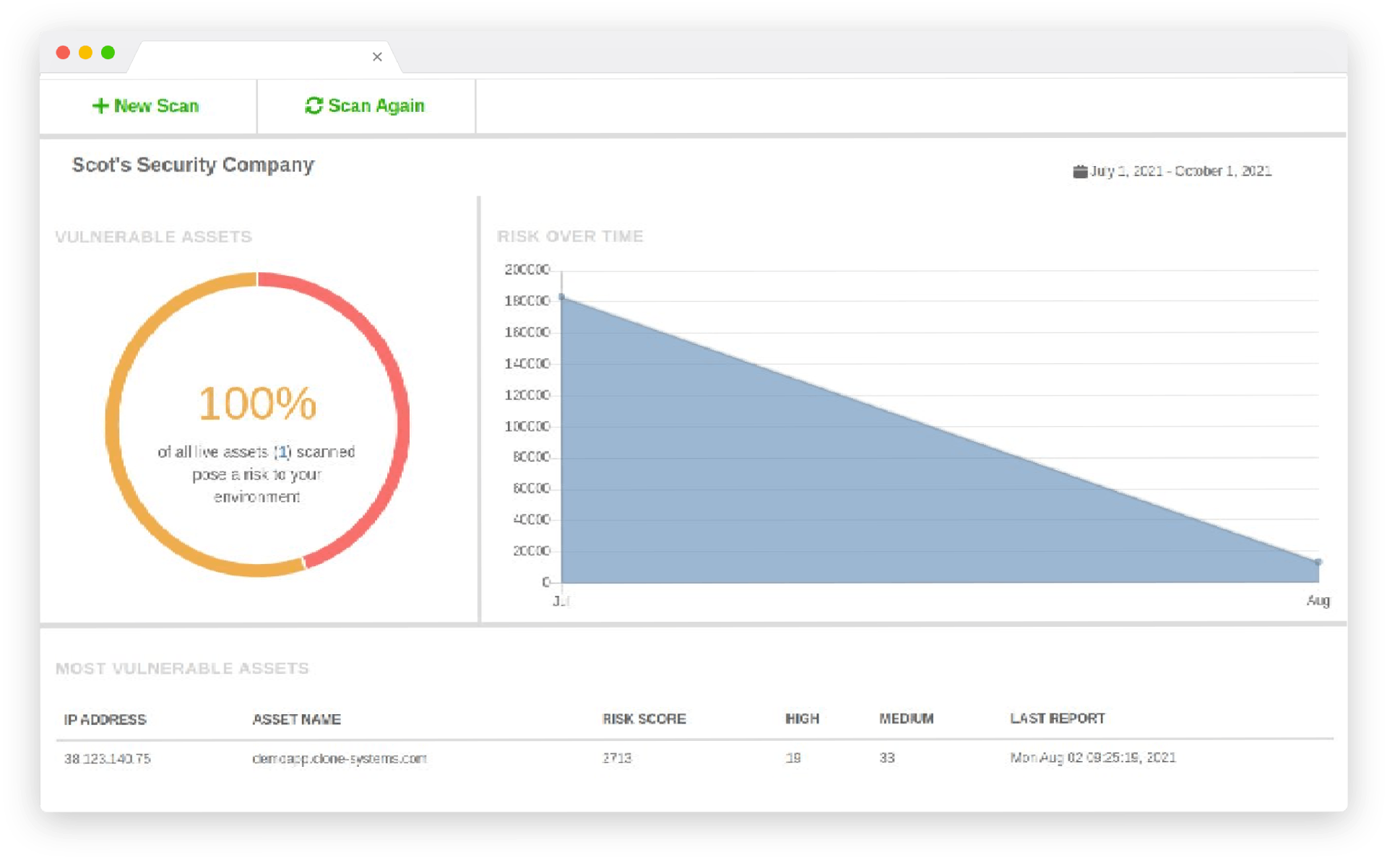
Vulnerability Assessment
Identify and prioritize vulnerabilities in your infrastructure, applications, and endpoints. Our expert team provides actionable recommendations to remediate identified vulnerabilities, helping you maintain compliance and avoid potential data breaches. Partner with us to gain peace of mind and protect your critical assets from emerging threats.
What is SOC as a Service?
The ability of an organization to run an effective and mature SOC in-house is influenced by a number of factors. Because of the cybersecurity talent shortage, attracting and retaining skilled personnel is difficult and expensive.
Effective Cybersecurity necessitates the purchase of a variety of security solutions aimed at addressing and mitigating a wide range of potential threats.
Offerings such as SOC-as-a-Service allow a company to delegate its security responsibilities to a third-party provider. Rather than staffing a full-service SOC in-house, the SOC-as-a-Service provider manages the round-the-clock network monitoring and defense required to combat modern cyber threats.
What is SOC as a Service?
The ability of an organization to run an effective and mature SOC in-house is influenced by a number of factors. Βecause of the Cyber Security talent shortage, attracting and retaining skilled personnel is difficult and expensive.
Effective Cyber Security necessitates the purchase of a variety of security solutions aimed at addressing and mitigating a wide range of potential threats.
Offerings such as SOC-as-a-Service allow a company to delegate its security responsibilities to a third-party provider. Rather than staffing a full-service SOC in-house, the SOC-as-a-Service provider manages the round-the-clock network monitoring and defense required to combat modern cyber threats.
Benefits of SOC-as-a-Service
Improved Security Staffing
Many organizations are having difficulty attracting and retaining skilled security personnel due to the ongoing cybersecurity skills shortage. An organization’s existing security team can be supplemented and gaps filled by partnering with a managed SOC provider.
Lower TCO
Deploying, maintaining, and operating a complete SOC in-house can be costly. Organizations can share the cost of equipment, licenses, and payroll with the other customers of their managed SOC provider. Strong cybersecurity costs less in terms of both capital and operational expenditures.
Access to Security Expertise
Specialized security experts, such as incident responders, malware analysts, and cloud security architects, are occasionally required by organizations. These skill sets can be hard to come by and even harder to keep. When customers need skilled cybersecurity specialists, a SOC-as-a-Service provider can provide them.
Increased Security Maturity
It takes time to develop the solutions and institutional knowledge needed for a mature cybersecurity program. By giving an organization access to their provider’s existing solution stack and security experts, partnering with a SOC-as-a-Service provider can help to expedite this process.
Up-to-Date Security
With an organization’s limited IT and security budget, staying current with the latest SOC tools and capabilities can be difficult. A managed SOC, on the other hand, has the resources to keep its toolset current and provide customers with the advantages of cutting-edge security.
Benefits of SOC-as-a-Service
Improved Security Staffing
Many organizations are having difficulty attracting and retaining skilled security personnel due to the ongoing cybersecurity skills shortage. An organization’s existing security team can be supplemented and gaps filled by partnering with a managed SOC provider.
Increased Security Maturity
It takes time to develop the solutions and institutional knowledge needed for a mature cybersecurity program. By giving an organization access to their provider’s existing solution stack and security experts, partnering with a SOC-as-a-Service provider can help to expedite this process.
Up-to-Date Security
With an organization’s limited IT and security budget, staying current with the latest SOC tools and capabilities can be difficult. A managed SOC, on the other hand, has the resources to keep its toolset current and provide customers with the advantages of cutting-edge security.
Lower TCO
Deploying, maintaining, and operating a complete SOC in-house can be costly. Organizations can share the cost of equipment, licenses, and payroll with the other customers of their managed SOC provider. Strong cybersecurity costs less in terms of both capital and operational expenditures (CapEx/OpEx).
Access to Security Expertise
Specialized security experts, such as incident responders, malware analysts, and cloud security architects, are occasionally required by organizations. These skill sets can be hard to come by and even harder to keep. When customers need skilled cybersecurity specialists, a SOC-as-a-Service provider can provide them.