Managed SIEM Providers
What is Managed SIEM?
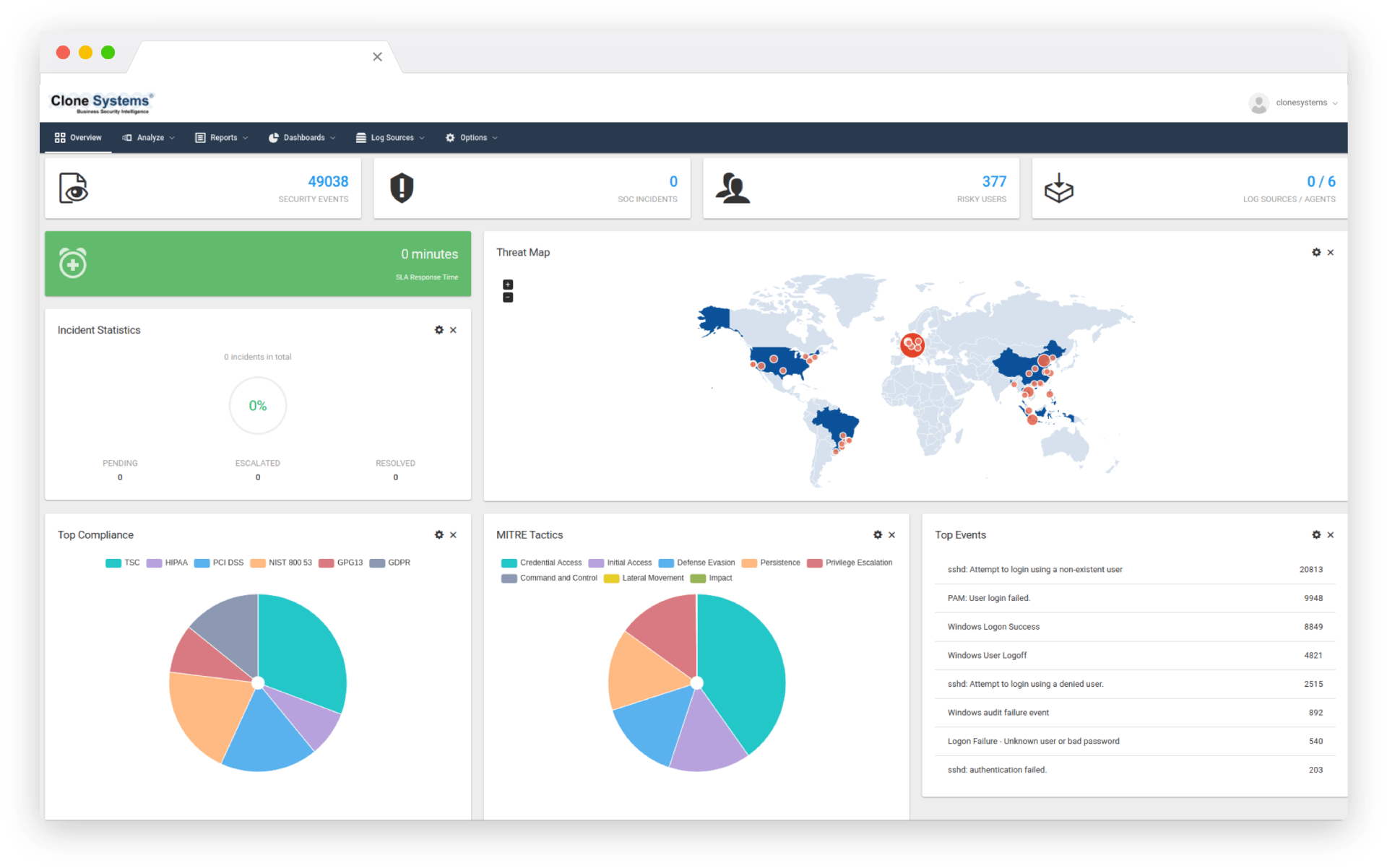
Security Information and Event Management (SIEM) software solutions are used by businesses of all sizes to detect and respond to finformation technology security threats. SIEM tools are defined by their ability to collect data from all IT assets on the network in the form of event logs. This is presented in a centralized interface that a skilled security analyst can manipulate and organize to identify Indicators of Compromise (IoC).
SIEM technologies combine the capabilities of two distinct types of legacy information technology security tools:
- Security Event Management (SEM) software, that enables real-time analysis of event, application, and system logs.
- Security Information Management (SIM) software, which is used to retrieve and analyze log data and generate structured reports based on specified parameters.
SIEM tools combine these two capabilities to provide real-time incident monitoring and threat detection capabilities, as well as streamline features for manual analysis of security logs and events. Managed SIEM is an alternative to deploying, configuring, and monitoring a SIEM software solution on-premises. It involves an organization contracting with a third-party service provider to host a SIEM application on their servers and monitor the organization’s network for potential security threats. Managed SIEM enables organizations to deploy more quickly, reduce setup and training costs, and leverage the expertise of cyber security specialists.
Why Managed SIEM?
No Resources
The majority of small businesses lack the resources necessary to handle all of the functions offered by managed SIEM services. A small business may be completely devoid of dedicated IT personnel. Even if it does have some, they are almost certainly already swamped with other IT-related tasks.
This may include implementing new software strategies and conducting research to determine the optimal product stack for business operations. Oftentimes, there is simply not enough time in the day to monitor and respond to all network events.
Identifying and resolving network vulnerabilities is one of the responsibilities of information technology professionals. However, with limited resources and an expanding IT scope, many CIOs lack the resources necessary to devote to identifying vulnerable systems. Again, this is a function that third-party managed SIEMs are capable of performing.
They scan the network for vulnerabilities and then address them, decreasing the likelihood of a breach over time.
Lack of Time
Each product is unique, and IT professionals may need to spend days or even weeks learning how to use it effectively. Additionally, the software requires a substantial amount of labor time from a business. Because most SIEM systems do not perform this function automatically, cybersecurity personnel must physically sit there monitoring logs and investigating threats.
In a small business, IT professionals need to focus on tasks that add the most value to the organization, not on network monitoring. Thus, many businesses choose a managed approach due to a lack of time.
Managed SIEM services are capable of performing tasks such as behavioral monitoring and quickly identifying unusual network activity. Third-party operators can notify and alert immediately if suspicious behavior is observed. This allows for immediate action and resolution upon occurrence.
Budget restrictions
Hiring IT staff to monitor the network is costly. Only the largest and most profitable businesses are capable of bringing it in-house. As a result, the vast majority of businesses opt for managed services. While managed SIEM services are significantly less expensive than hiring a new full-time employee, they provide many of the same benefits.
Managed SIEM services rely on dedicated teams of analysts who split their time between multiple clients. Intelligent software feeds events to these analysts, who then analyze and report on them to businesses. Frequently, managed SIEM services will take action on behalf of the company to protect the network.
What makes managed SIEM services interesting is that they can help businesses improve both productivity and security. Consider the case where a company utilizes a managed SIEM provider to manage its firewall.
While firewalls are excellent at preventing unwanted traffic, they have a nasty habit of blocking a variety of other things that need to enter and exit a network – such as traffic that has not been classified as good or bad yet, or an attack method that the firewall is unaware of yet.
Managed SIEM services can update firewall settings and other security settings across an IT landscape, allowing critical data to pass through while also tuning the system to avoid infection with malware and viruses. Managed SIEM can assist in capitalizing on all priorities and maximizing the efficiency of IT resources.
What are the Benefits of Managed SIEM?
SIEMs aide in the effective operation of the Security Operations Center (SOC). They enable, in particular:
- Improved Security Data. SIEMs consolidate security data, enhance analysis, and use incident response workflows. This can also result in increased visibility across the enterprise’s entire security landscape. Additionally, the SIEM typically normalizes security. The multiple data streams that feed into the SIEM have distinct schemas and fields in their raw form. It is not accepted as normal. For instance, user data originating from network logs, email servers, databases, and mobile devices may take on a variety of forms. This introduces a complication into data analysis and event correlation. The SIEM can reformat data to make it more consistent for incident analysts and response processes. A related benefit is data storage. For extended analytics and reporting, the SIEM can store normalized security data. This could also aid in compliance.
- Enhancing Network Visibility. SIEM log management and aggregation simplify the process of obtaining a network overview. Indeed, given the complexity and diversity of modern networks, it is quite possible for a network to contain “dark spaces.” As a result, network managers and security teams lose visibility into what is actually happening with databases, servers, devices, and third parties as the network scales. Hackers are on the lookout for dark spots on networks. It enables them to conceal persistent threats and traverse digital assets laterally without being detected. SIEM mitigates this risk by collecting data about security events from across the network. It then centralizes and analyzes the data. SIEM log analysis can shed light onto these shadowy areas.
- More Accurate Threat Detection and Security Alerting. SIEM tools can use their massive data sets to detect and identify threats more precisely than individual security data streams could. Additionally, they are capable of enriching security event data and providing critical context for incident alerts. For instance, a SIEM can correlate a threat signature discovered in one log with a threat discovered in another log.
- Faster, more efficient SecOps. With a SIEM sifting through millions of data points, SOC analysts can quickly act by utilizing analysis templates to rapidly analyze log and threat intelligence data. This can save both time and money in regards to security threat response and negative cyberattack impacts. Without a SIEM, security analysts would be forced to manually interpret logs from multiple security devices and data sources, such as threat intelligence feeds. Along with exhausting people — a significant issue in and of itself — it significantly slows down the incident response process. By configuring the SIEM tool to respond in real time to incidents, data loss is prevented.
- Improved Compliance. Regulations and compliance frameworks such as HIPAA, invariably mandate security data logging as a critical control. SIEMs fulfill this role by streamlining the attestation process through the use of pre-defined compliance reporting templates.
Managed Security Services vs SIEM
What is the difference between a Managed Security Information and Event Management (SIEM) and a Managed Security Service Provider (MSSP)?
The most fundamental Managed SIEM providers host the SIEM tool, manage the collection of security and event logs, and provide reporting on the results. These providers can either manage a centralized SIEM that monitors the networks of multiple customers, or they can configure and manage individualized SIEM platforms for each customer.
An MSSP typically provides a broader range of services and a higher level of service. They may take a more active role in analyzing log data and investigating security threats in addition to hosting and managing a SIEM tool. Additionally, they may offer a broader range of services, such as anti-malware software and vulnerability scanning.
When choosing whether to contract with a Managed SIEM provider or MSSP, the most important thing is to assess the overall service offerings to ensure there is a good value-for-money and security coverage that complements the capabilities of an existing SecOps team.
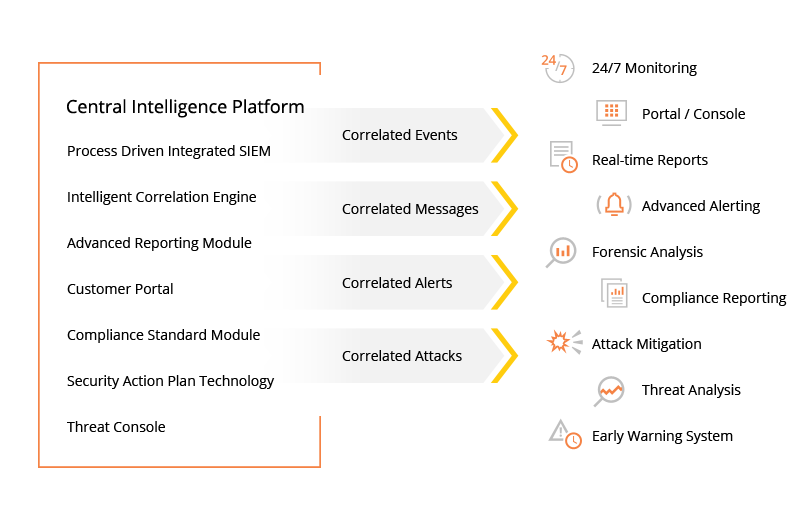
CloneGuard Managed SIEM
CloneGuard Security Operation Center (SOC) consistently monitors, analyzes and triages the correlated events 24/7 so that they can escalate prioritized alerts to your team as needed in order to help identify and prevent emerging threats before they occur.
Start monitoring your external and internal attack surface on a regular basis with CloneGuard Managed SIEM.





