Managed SIEM
Real-time analysis of threats, by correlating historical and real-time security information and analyzing correlated events to help prevent emerging threats.
Talk with our experts

Managed SIEM
Real-time analysis of threats, by correlating historical and real-time security information and analyzing correlated events to help prevent emerging threats.
Customers Around the World
Data Correlation
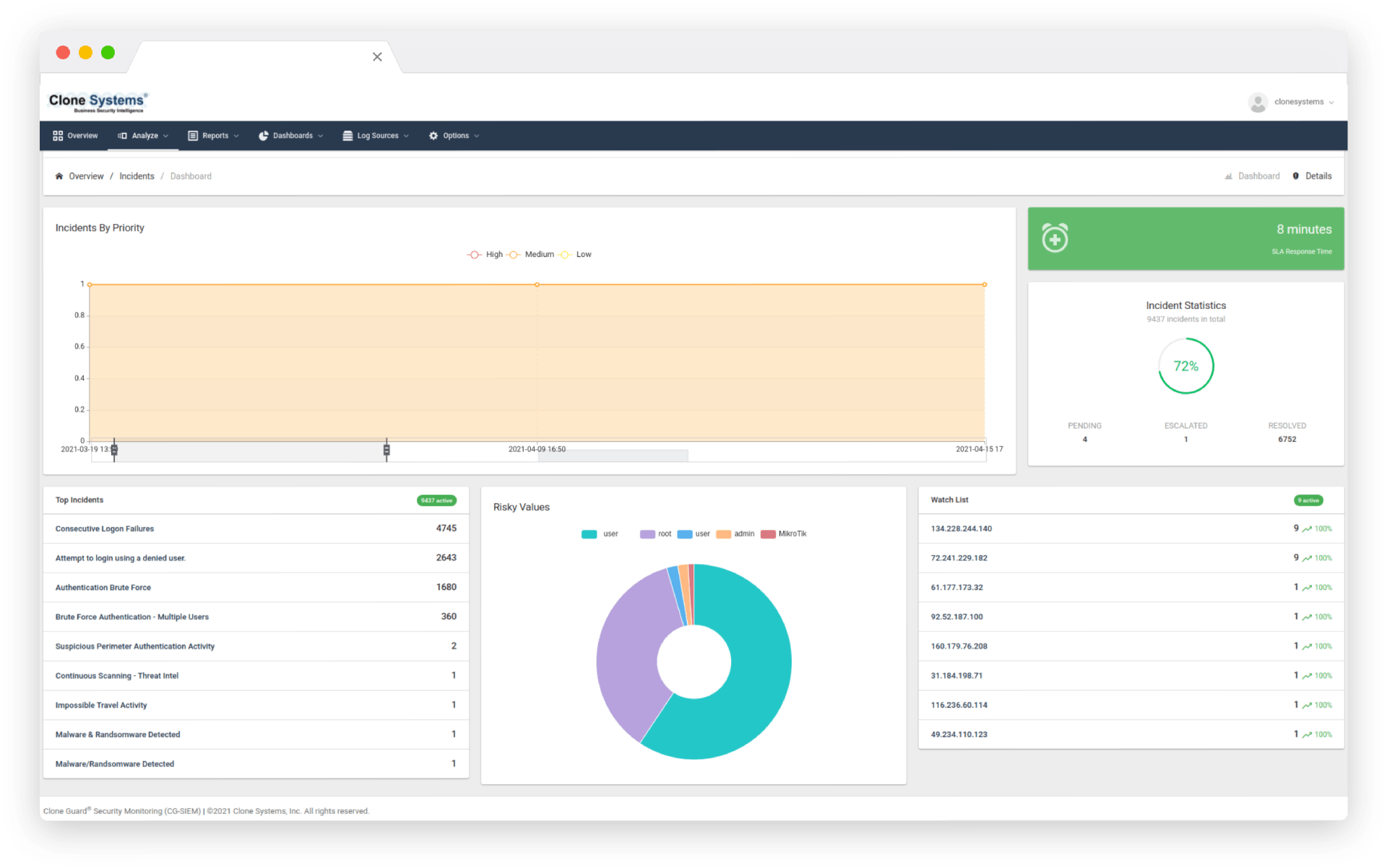
Optimize Your Security Intelligence
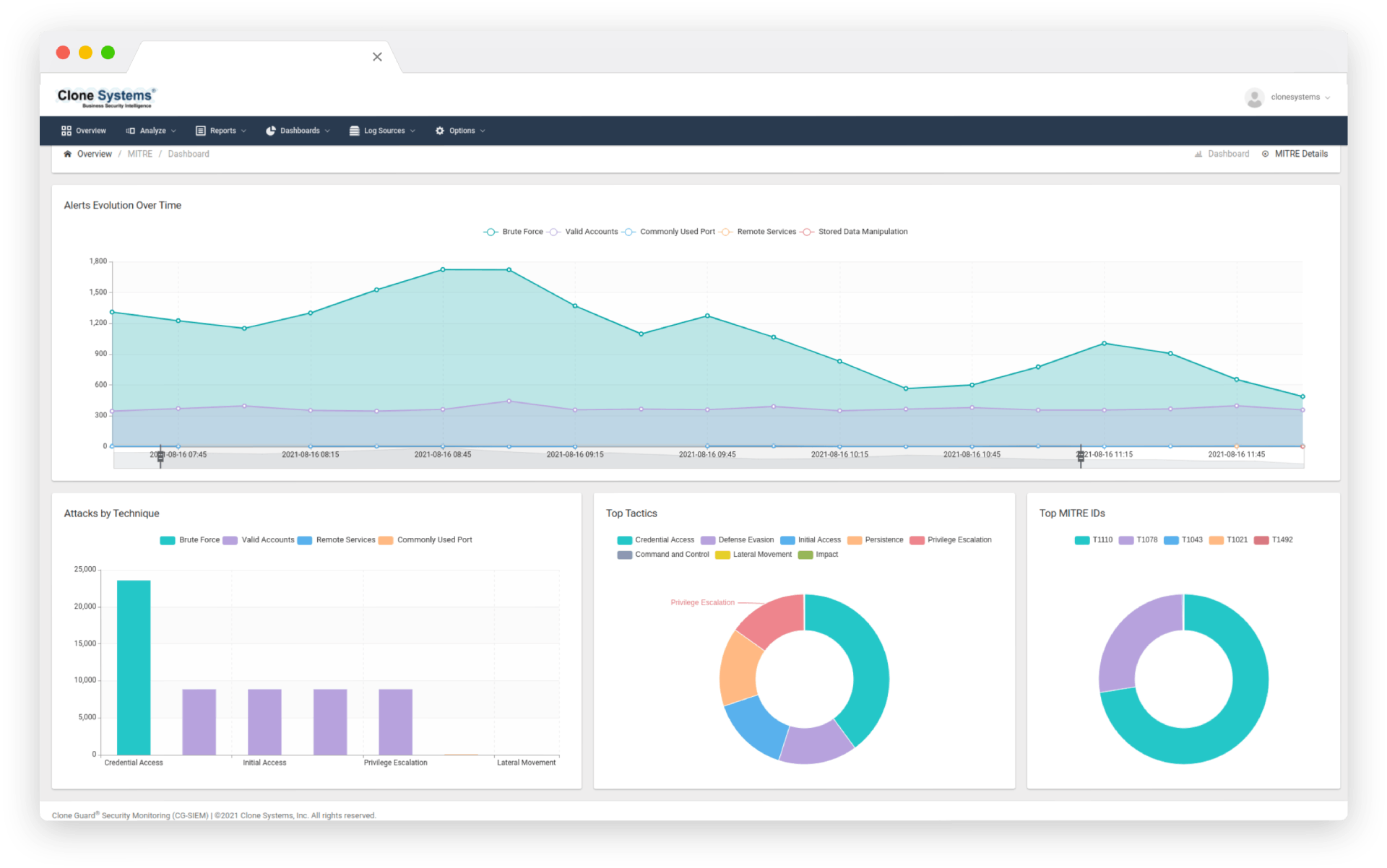
Correlate historical and real-time security information to identify patterns and trends to help prevent emerging threats. Analyze correlated events to investigate suspicious activity and determine the level of potential risk to the business. Active threat intelligence is consistently updated from multiple internal/external security sources.
SOC MONITORING
Defend against advanced threats
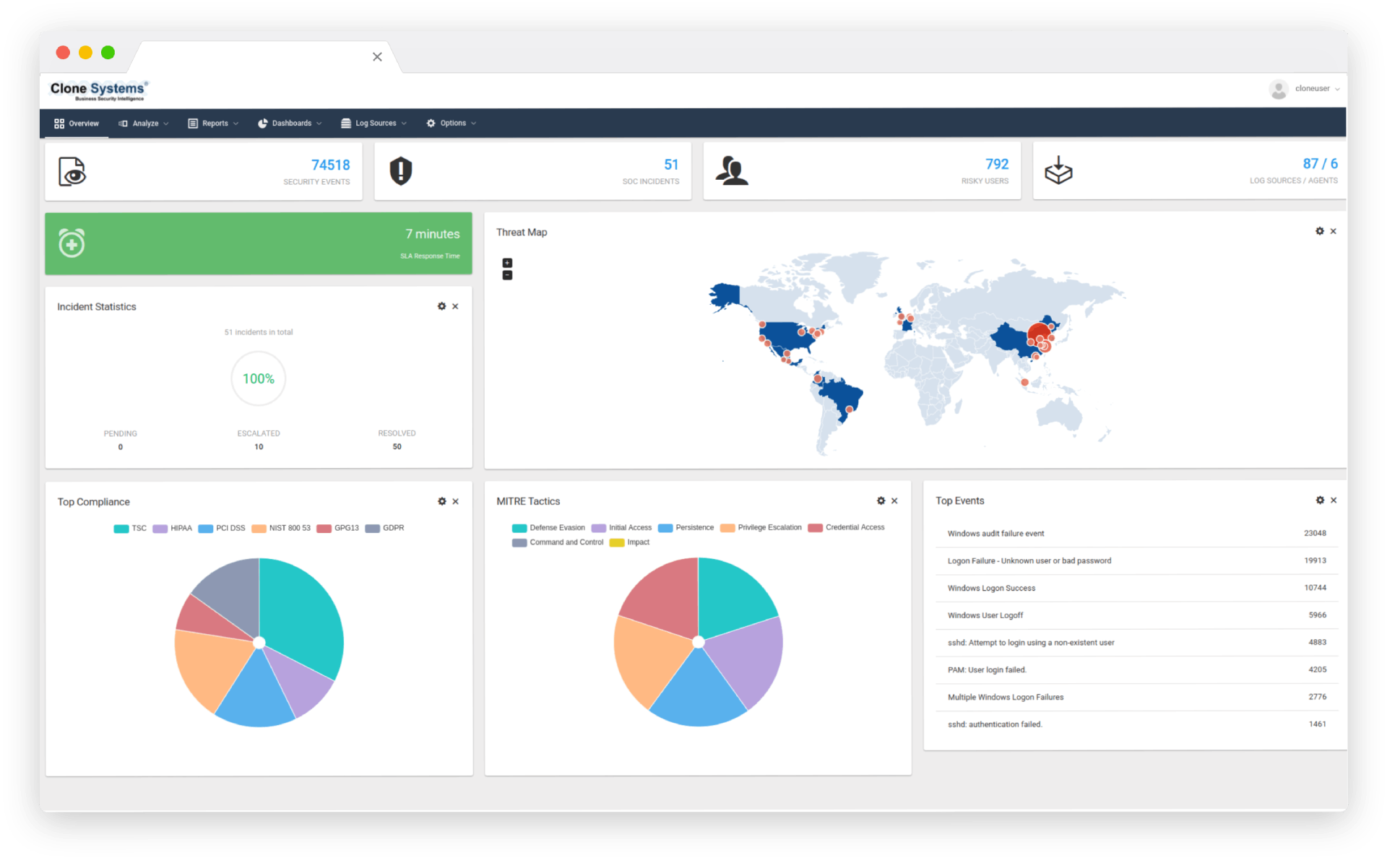
Monitoring and alerting to identify events that require additional investigation by your team. SOC monitoring and analyzing your correlated events to identify and triage event patterns. Unified reporting of correlated security events occurring on your network. Intrusion Detection the EDR agent scans the monitored systems looking for malware, rootkits, and suspicious anomalies. It can detect hidden files, cloaked processes, unregistered network listeners, and inconsistencies in system call responses.
Log collection and storage
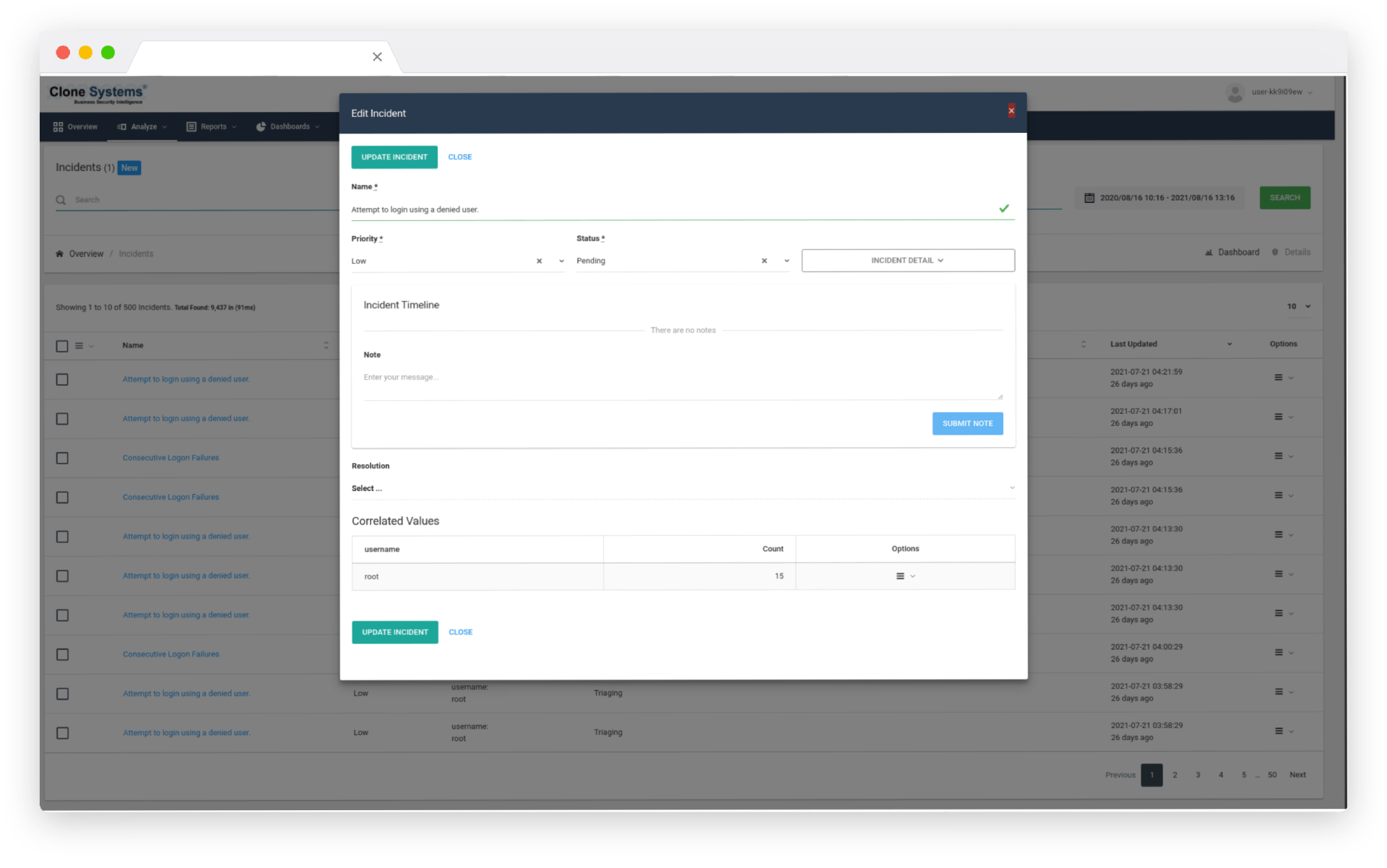
Aggregate and Analyze Your Security Logs
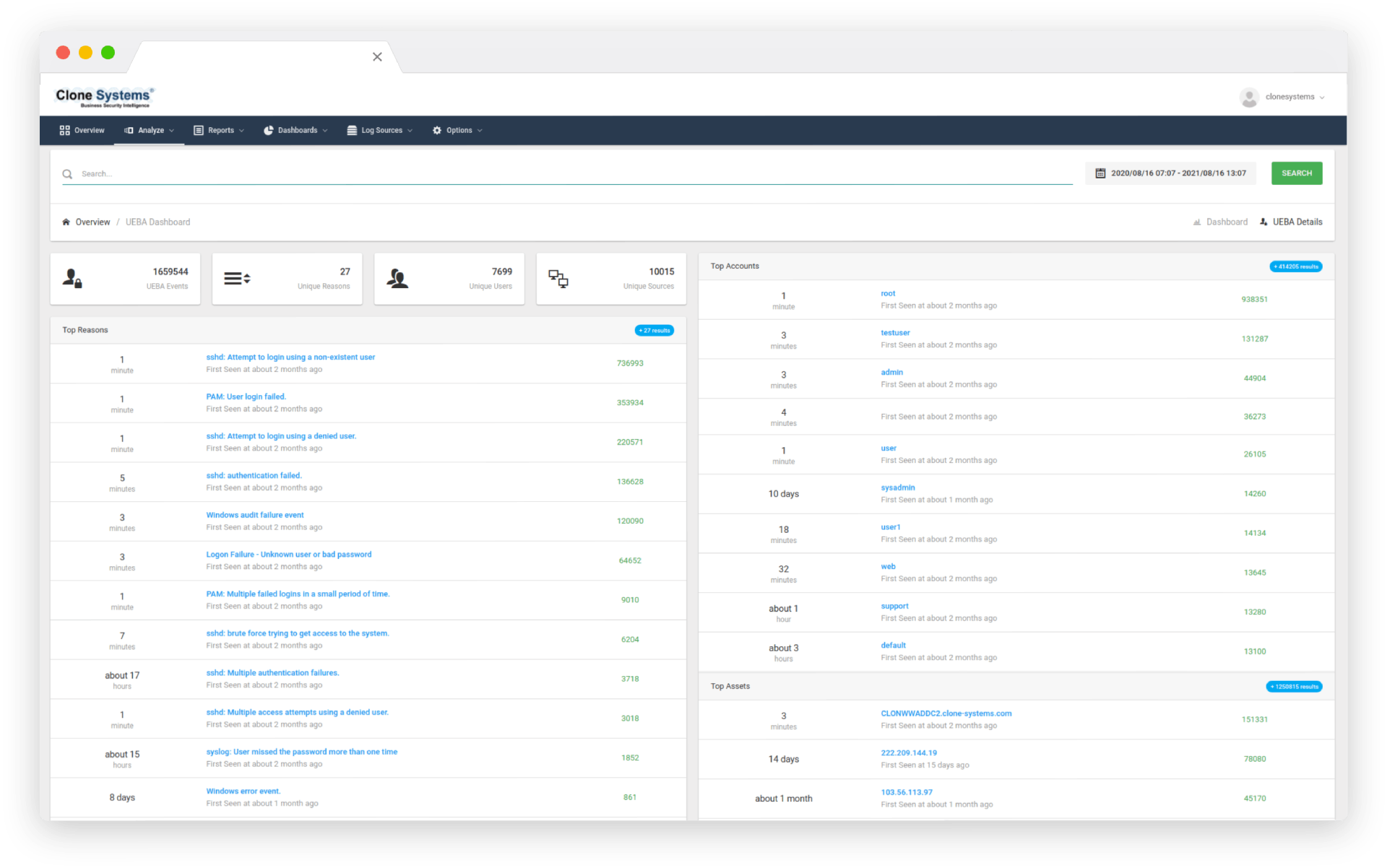
Log collection and storage with robust parsing, classifying, and categorizing capabilities allow you to quickly identify vulnerabilities in your environment and be capable of scaling as you grow. For example, for File Integrity Monitoring, the EDR agent monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on.
In addition, it natively identifies users and applications used to create or modify files. Regarding Vulnerability Detection, The EDR agents pull software inventory data and send this information to the SIEM, which correlates with continuously updated CVE databases to identify well-known vulnerable software and operating system issues.
Data Correlation
Optimize Your Security Intelligence
Correlate historical and real-time security information to identify patterns and trends to help prevent emerging threats. Analyze correlated events to investigate suspicious activity and determine the level of potential risk to the business. Active threat intelligence is consistently updated from multiple internal/external security sources.
SOC MONITORING
Defend against advanced threats
Monitoring and alerting to identify events that require additional investigation by your team. SOC monitoring and analyzing your correlated events to identify and triage event patterns. Unified reporting of correlated security events occurring on your network. Intrusion Detection the EDR agent scans the monitored systems looking for malware, rootkits, and suspicious anomalies. It can detect hidden files, cloaked processes, unregistered network listeners, and inconsistencies in system call responses.

LOG COLLECTION AND STORAGE
Aggregate and Analyze Your Security Logs
Log collection and storage with robust parsing, classifying, and categorizing capabilities allow you to quickly identify vulnerabilities in your environment and be capable of scaling as you grow. For example, for File Integrity Monitoring, the EDR agent monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on.
In addition, it natively identifies users and applications used to create or modify files. Regarding Vulnerability Detection, The EDR agents pull software inventory data and send this information to the SIEM, which correlates with continuously updated CVE databases to identify well-known vulnerable software and operating system issues.
Maximize Your Teams Visibility
Correlate historical and real-time security information to identify patterns and trends to help prevent emerging threats.


Talk with our experts
Maximize Your Teams Visibility
Correlate historical and real-time security information to identify patterns and trends to help prevent emerging threats.
Identify incidents by members of your team

SOC monitoring and analyzing data real-time

Escalation and reporting of correlated incidents

Analyzing correlated events to investigate suspicious activity

Benefits
Easy no hassle automated setup
On-prem, Cloud (Azure, AWS, private), virtual
Meets all compliance & privacy requirements
Your security is our responsibility
Transparent access to all of your data
Features
Includes Hardware & Software
EDR Agents (Windows, MacOS, Linux)
Security Orchestration Platform
SOC engineers 24/7 stopping threats
Darkweb Probing
What is Managed SIEM and how does it work?
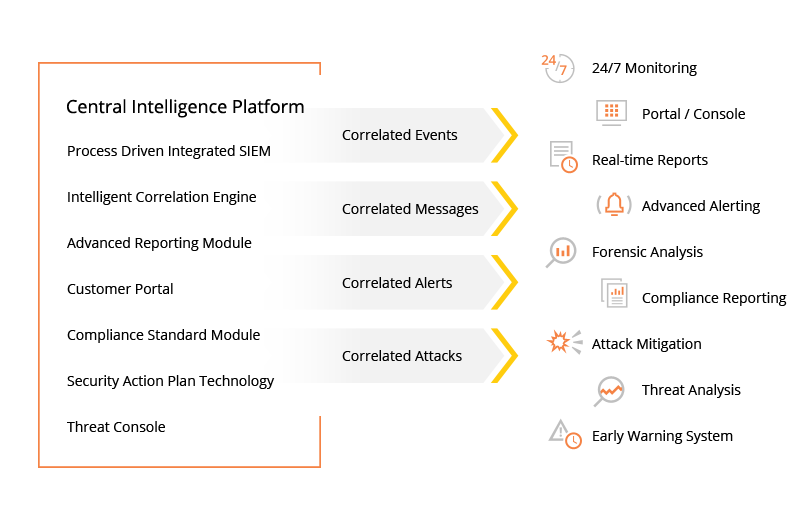
The Security Information and Event Management (SIEM) solution is built on top of our Log Management solution’s robust parsing, normalization, classification, and categorization capabilities.
It actively inspects and correlates your historical and real time logs collected from your devices against consistently updated threat intelligence feeds, security signatures, and anomaly detection events to identify unique threat patterns and trends that could negatively impact your security.
Our intuitive SIEM solution presents this correlated log data and any identified threat patterns to facilitate a deeper level of troubleshooting and resolution.
Our Security Operation Center (SOC) consistently monitors, analyzes, and triages the correlated events 24/7 so that they can escalate prioritized alerts to your team as needed to help identify and prevent emerging threats before they occur.