Ethical Hacking
What is Ethical Hacking?
It’s easy to imagine a hacker sitting in a dark room trying to illegally breach a company’s security network or even conduct social engineering attacks to dupe individuals into disclosing their sensitive credentials.
In today’s digital landscape, Certified Ethical Hackers are increasingly working alongside cyber-aware organizations, to uncover security threats and improvements.
Because they work with organizations to improve network security, Ethical Hackers are often referred to as “White Hats.” Meanwhile, “Grey Hats” gain unauthorized access to networks but do not commit fraud, while “Black Hats” are evil third parties who aim to cause havoc in the name of “fame and fortune.”
With the owner’s consent, an Ethical Hacker can hack an organization’s systems to reveal network vulnerabilities while also testing and validating a business’s cyber security posture. An Ethical Hacker can help you determine how your personnel and business operations would fare in a real attack, allowing you to implement necessary countermeasures and staff training.
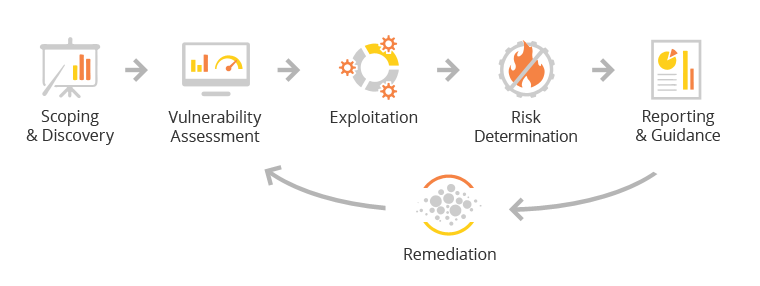
What types of ethical hacking exist?
There are two types of ethical hackers: Red Teaming and Offensive Security. For example, security research and penetration testing. They are inspired to carry out what a malicious actor may attempt on the same network.
Ethical hacking services include penetration testing of web applications and servers, systems, wireless networks, and social engineering strategies to gain unauthorized access to a network. For this reason, Penetration Testing is frequently the first choice of businesses.
A penetration test seeks to find flaws in your company’s infrastructure, apps, wireless, cloud, or workforce. The ability to examine your systems and devices through the eyes of a malicious third party will allow you to take the necessary remedial actions to minimize the risk of a breach.
In order to improve overall cyber-security and reduce the risk of data breaches, our SecOps team advises organizations to conduct penetration testing. The likelihood of a successful attack is greatly reduced by proactively identifying and resolving all existing vulnerabilities. To focus on the attack’s objectives rather than the attack’s methods, red teaming is a suitable service for organizations with mature security controls already in place.
Major Benefits of Ethical Hacking
Being proactive about cyber security is critical for business continuity in today’s increasingly digital world. By relying on their people and processes alone, companies can’t protect themselves from cyber-attacks.
It’s difficult for any in-house IT department to keep up with the constant stream of new malware, viruses, worms, and ransomware. This allows your company to stay ahead of the ever-changing threat landscape, identifying weak points and providing actionable advice to ensure you have adequate preventative measures in place moving forwards.
Hiring an Ethical Hacker protects your clients’ valuable assets and ensures that they feel secure working with you.

Clone Systems is Here to Help!
Clone Systems is QSTM Tiger Scheme certified. This certification is for technical security experts who want to demonstrate offensive security penetration testing skills. Our security team also holds CompTIA Network+ and CompTIA Security+ certifications, as well as the industry-recognized Certified Ethical Hacker (CEH) credential.
Contact our SOC team to learn more about how our highly qualified experts can help you test and protect your organization.





