Endpoint Detection & Response (EDR)
Protect your endpoints in real-time by identifying and preventing cyber attacks
Talk with our experts

Endpoint Detection & Response (EDR)
Protect your endpoints in real-time by identifying and preventing cyber attacks
Customers Around the World
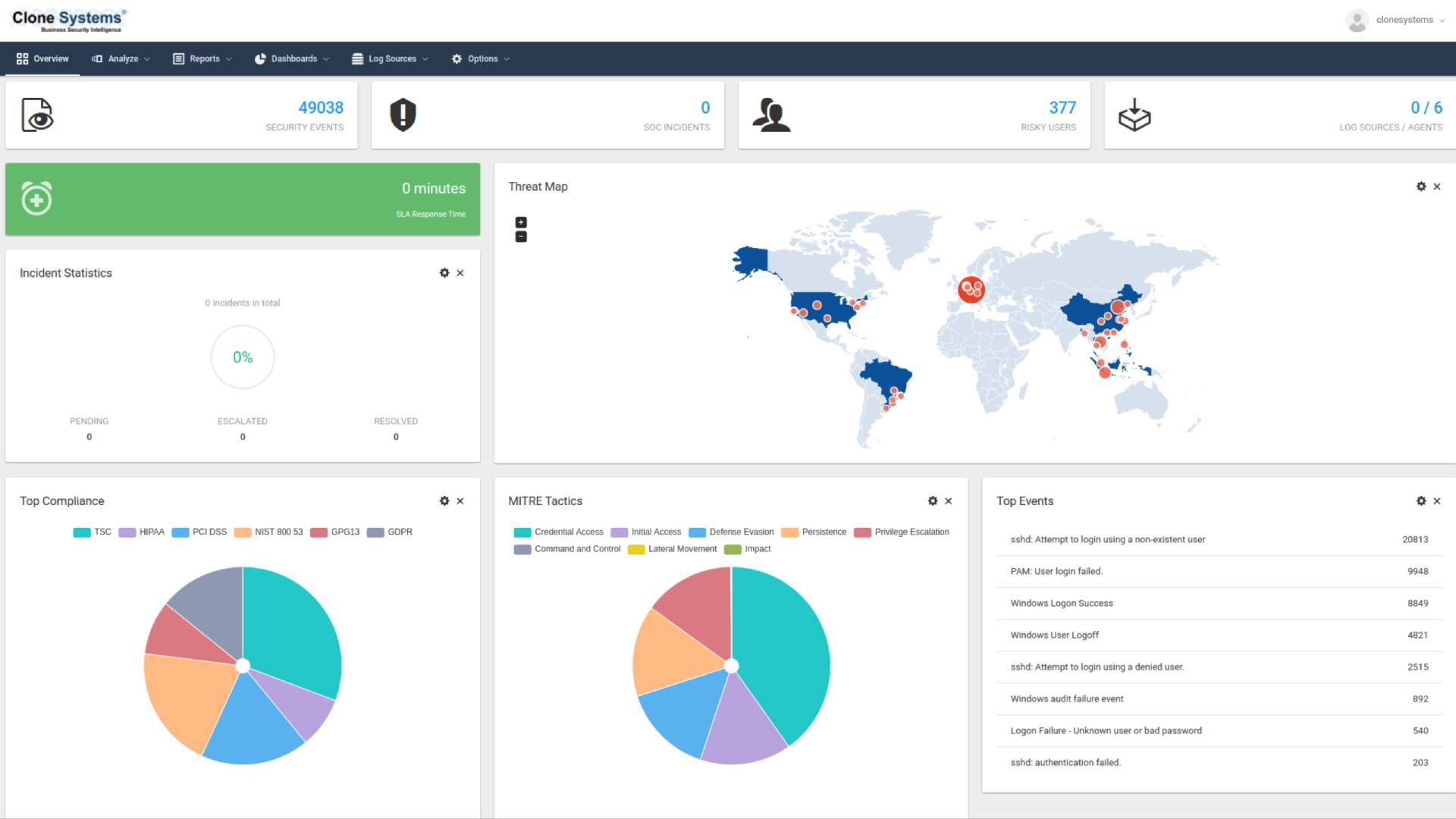
Real-time threat detection
Protect Your Endpoints
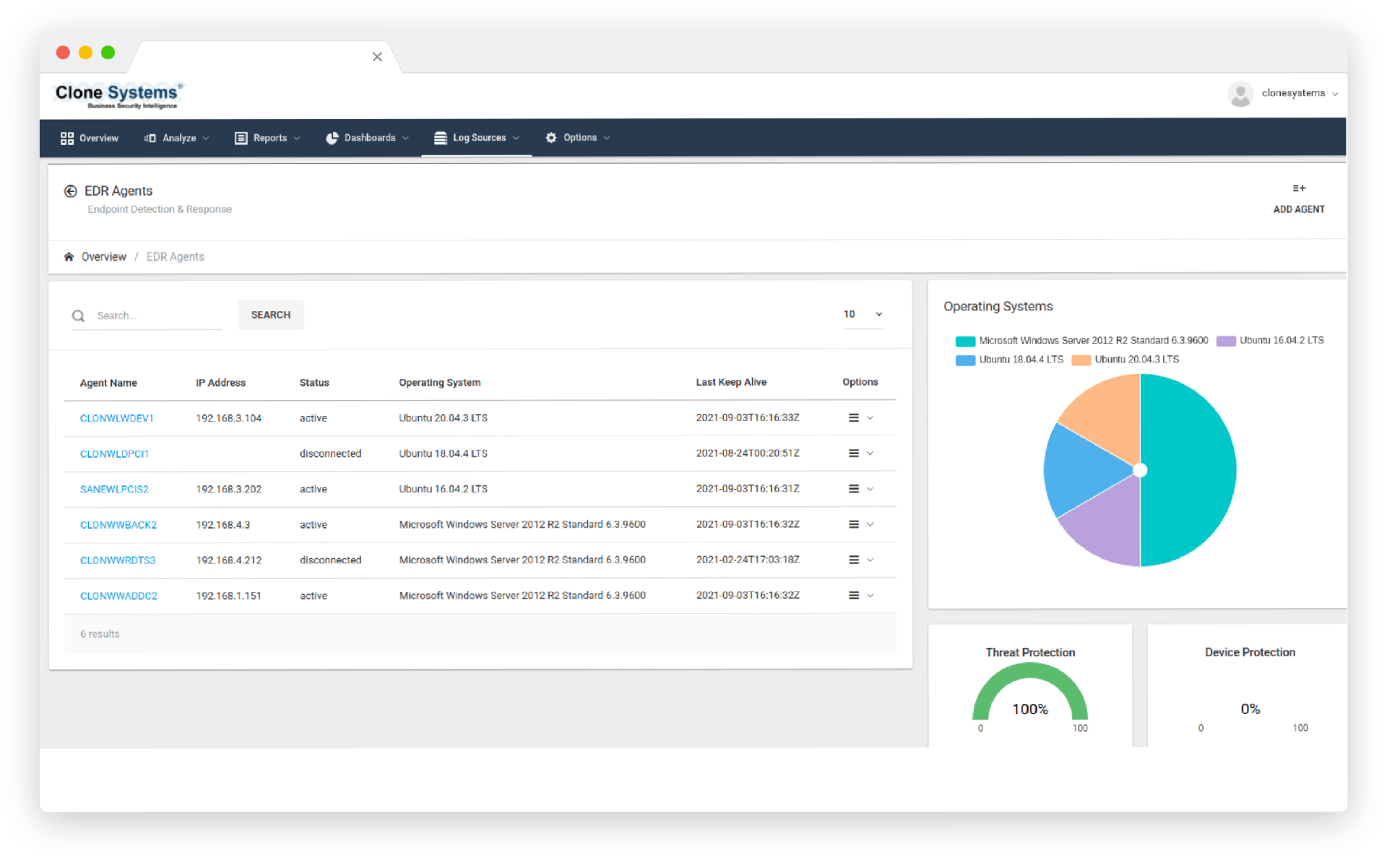
Real-time threat detection, analysis, and response protect your endpoints against all malicious threats. In addition, correlated threat intelligence provides a holistic view of known and unknown endpoint attacks, facilitating immediate corrective action against suspicious endpoint activity.
Real-time threat detection
Protect Your Endpoints
Real-time threat detection, analysis, and response protect your endpoints against all malicious threats. In addition, correlated threat intelligence provides a holistic view of known and unknown endpoint attacks, facilitating immediate corrective action against suspicious endpoint activity.
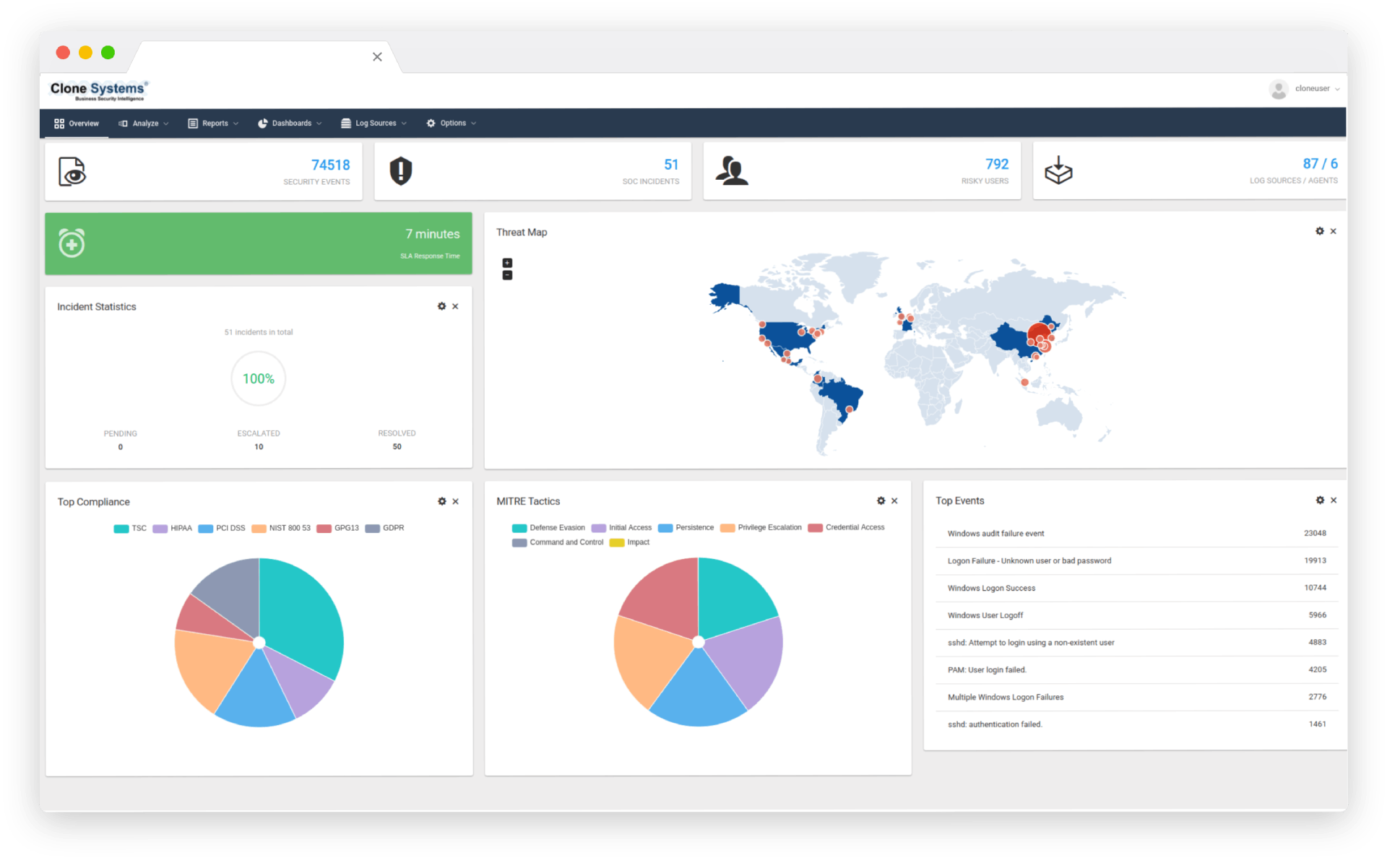
24/7 monitoring
Extend Your Security Resources
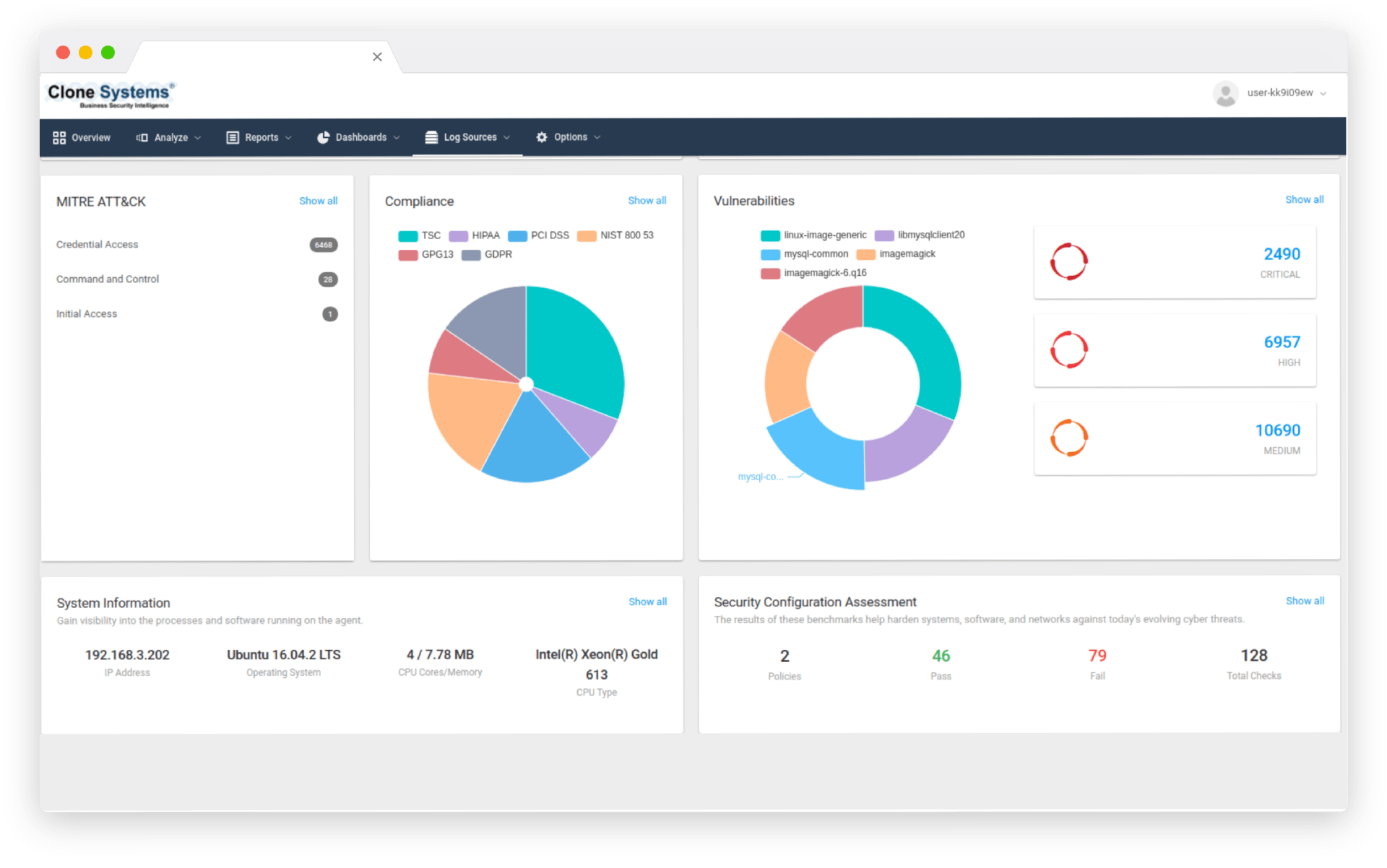
Leverage 24/7 monitoring, alerting, and reporting of suspicious endpoint behavior, across your enterprise. Free your team to focus on driving core business values with vendor-agnostic expertise with best-of-breed endpoint solutions managed by certified security engineers.
24/7 monitoring
Extend Your Security Resources
Leverage 24/7 monitoring, alerting, and reporting of suspicious endpoint behavior, across your enterprise. Free your team to focus on driving core business values with vendor-agnostic expertise with best-of-breed endpoint solutions managed by certified security engineers.

EDR PRODUCT SHEET
Download the EDR Product Sheet
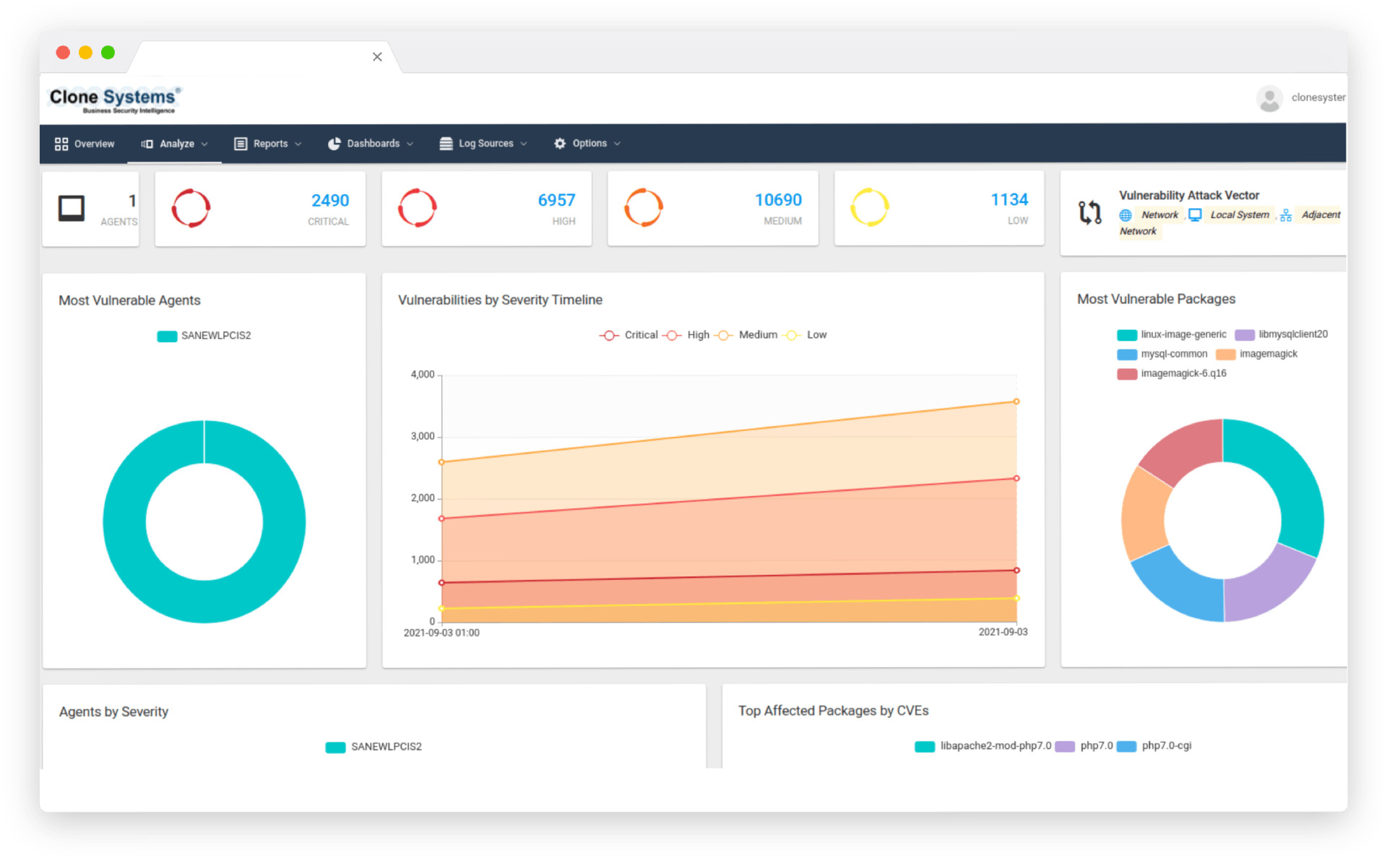
How the Endpoint Protection Service Works
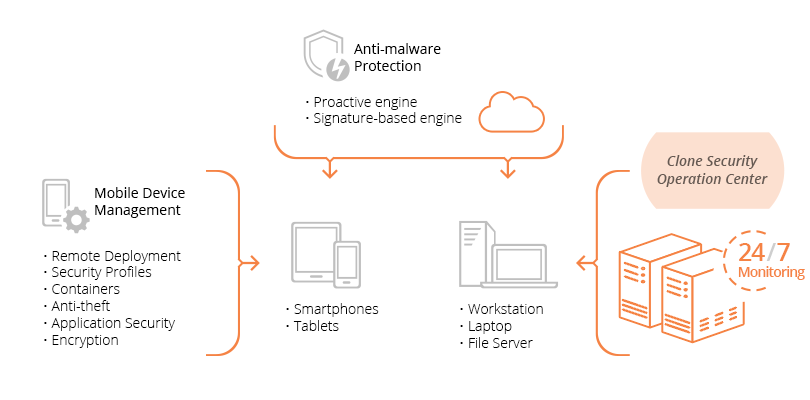
Our team of certified security engineers will work closely with your team to deploy your best-of-breed Advanced Endpoint Threat Protection solution across all your Windows, Mac, Linux, iOS, Android, and other mobile device endpoints using an intuitive management console.
Our EDR solution will protect endpoints in real-time from malware security threats using the latest correlated threat intelligence. In addition, the Clone Systems Security Operations Center (SOC) will consistently monitor the solution and endpoint activity 24/7.
If malware infects an endpoint, the Advanced Endpoint Threat Protection solution will quarantine the suspicious activity and the SOC can quickly contain and remediate the threat.