Security Orchestration Automation & Response (SOAR)
Maximize effectiveness and efficiency by streamlining people, processes, and technology with Clone’s SOAR tool.
Talk with our experts

Security Orchestration Automation & Response (SOAR)
Maximize effectiveness and efficiency by streamlining people, processes, and technology with Clone’s SOAR tool.
Customers Around the World
task automation
Boost productivity and efficiency
Eliminate errors through standardization and automation, while easing the burden on already overburdened SOC teams.
Reduce error-prone manual processes while maintaining consistency in incident response.
Automate repetitive tasks to maximize security staff efficiency.
task automation
Boost productivity and efficiency
Eliminate errors through standardization and automation, while easing the burden on already overburdened SOC teams.
Reduce error-prone manual processes while maintaining consistency in incident response.
Automate repetitive tasks to maximize security staff efficiency.
defend sophisticated attacks
Enhance the capability of your security team
Utilize our real-world, on-the-ground investigation experience and obtain the assistance necessary to fend off sophisticated attacks. With deployment, design, and pre-built playbooks, our teams will have an advantage over attackers.
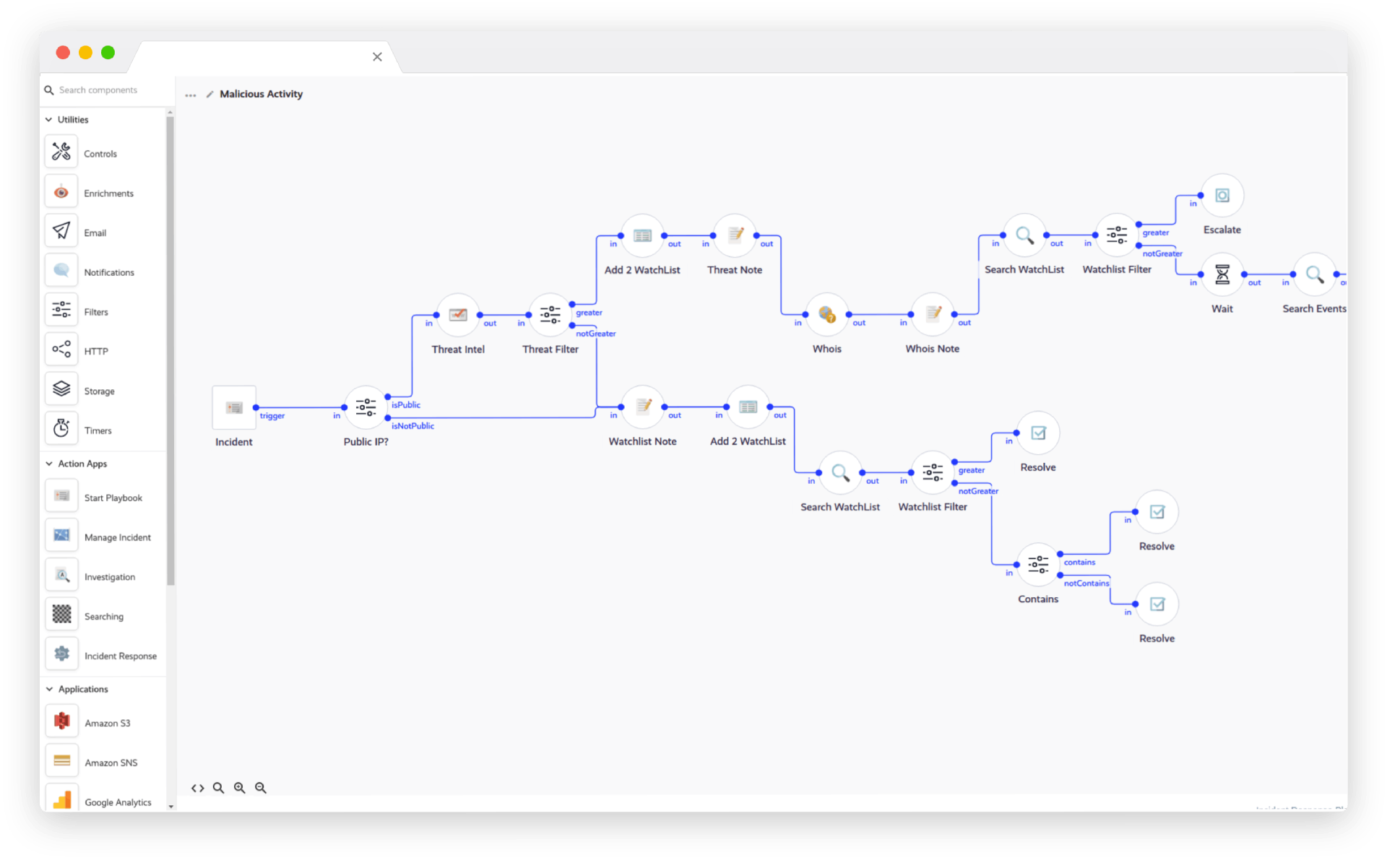
defend sophisticated attacks
Enhance the capability of your security team
Utilize our real-world, on-the-ground investigation experience and obtain the assistance necessary to fend off sophisticated attacks. With deployment, design, and pre-built playbooks, our teams will have an advantage over attackers.
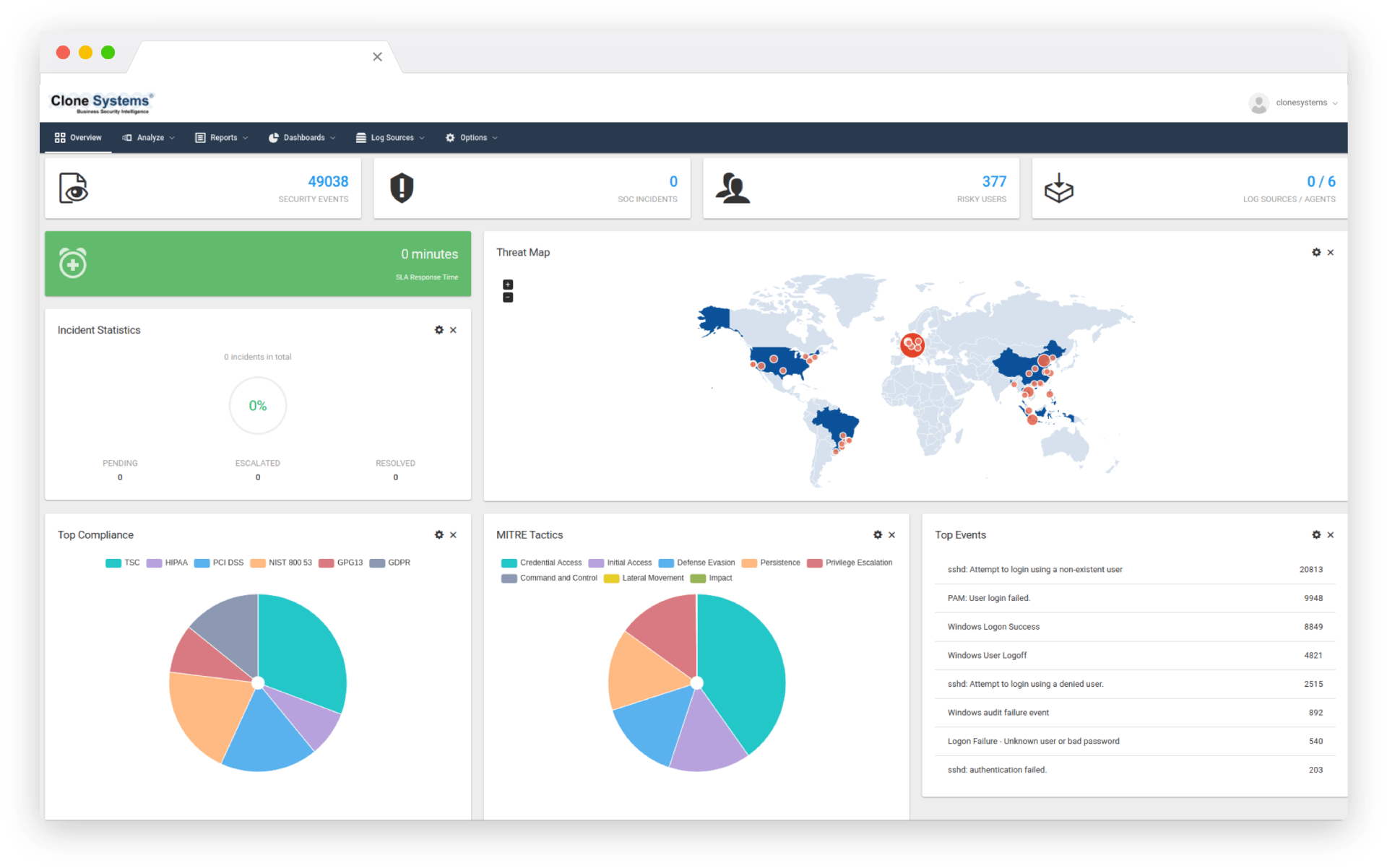
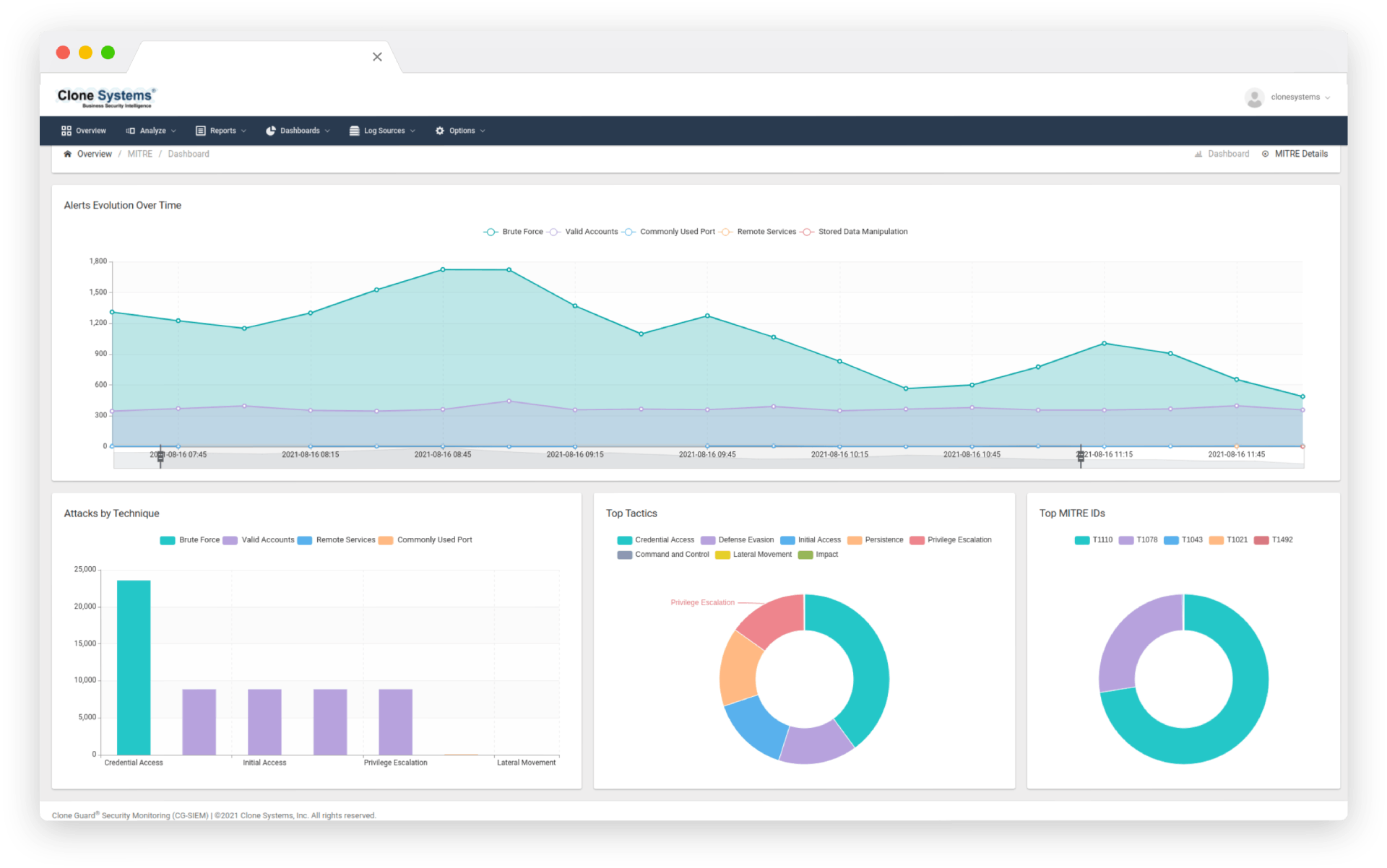
Defend against advanced threats
Correlate historical and real-time security information to identify patterns and trends to help prevent emerging threats.
Eliminate errors
through standardization and automation
Automate tasks
to maximize security staff efficiency.

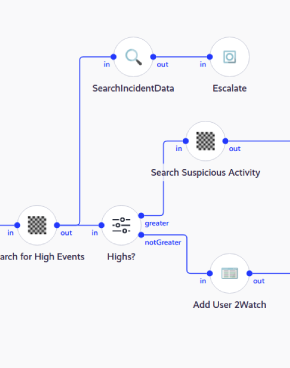
What is Security Orchestration Automation & Response (SOAR)?
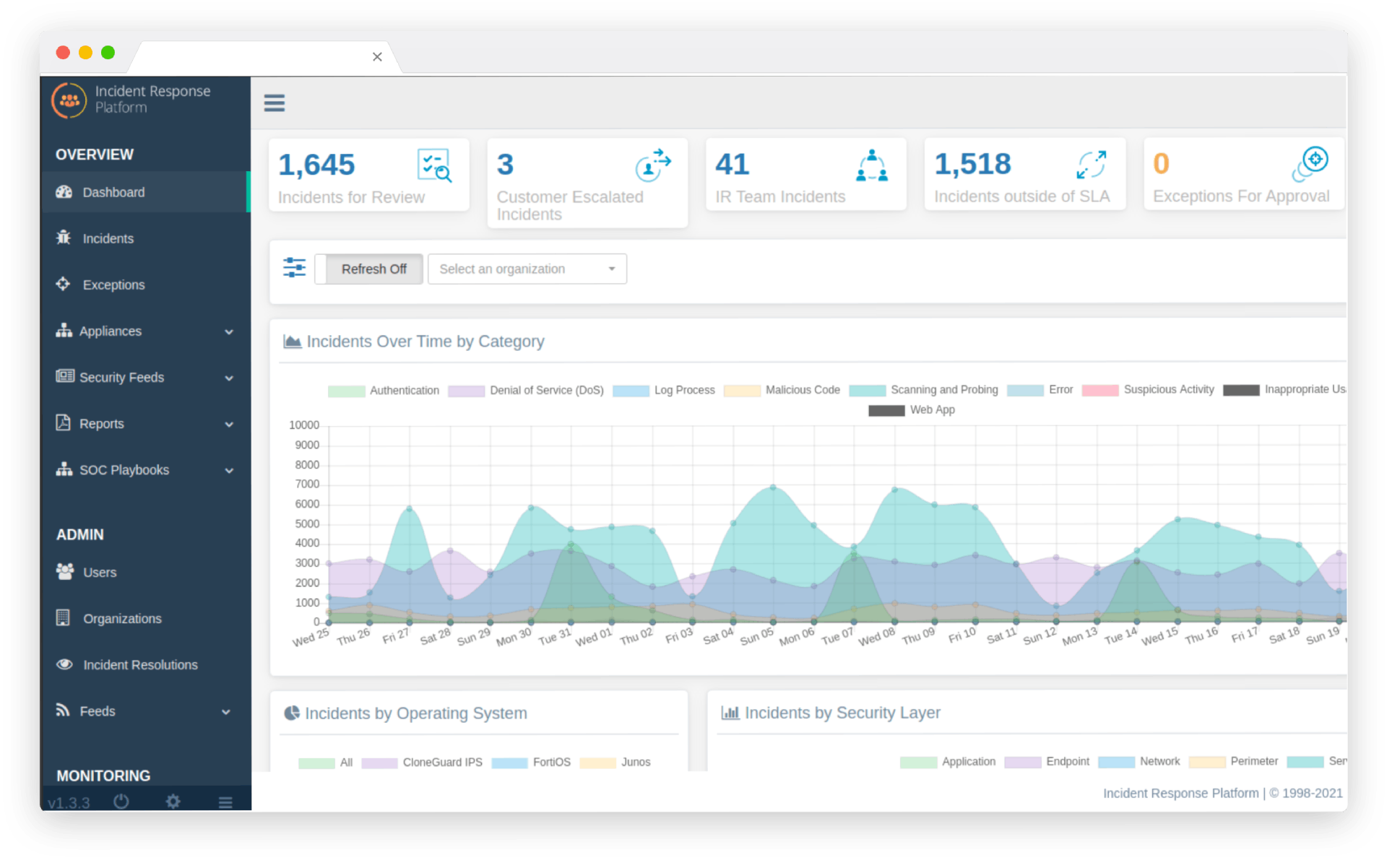
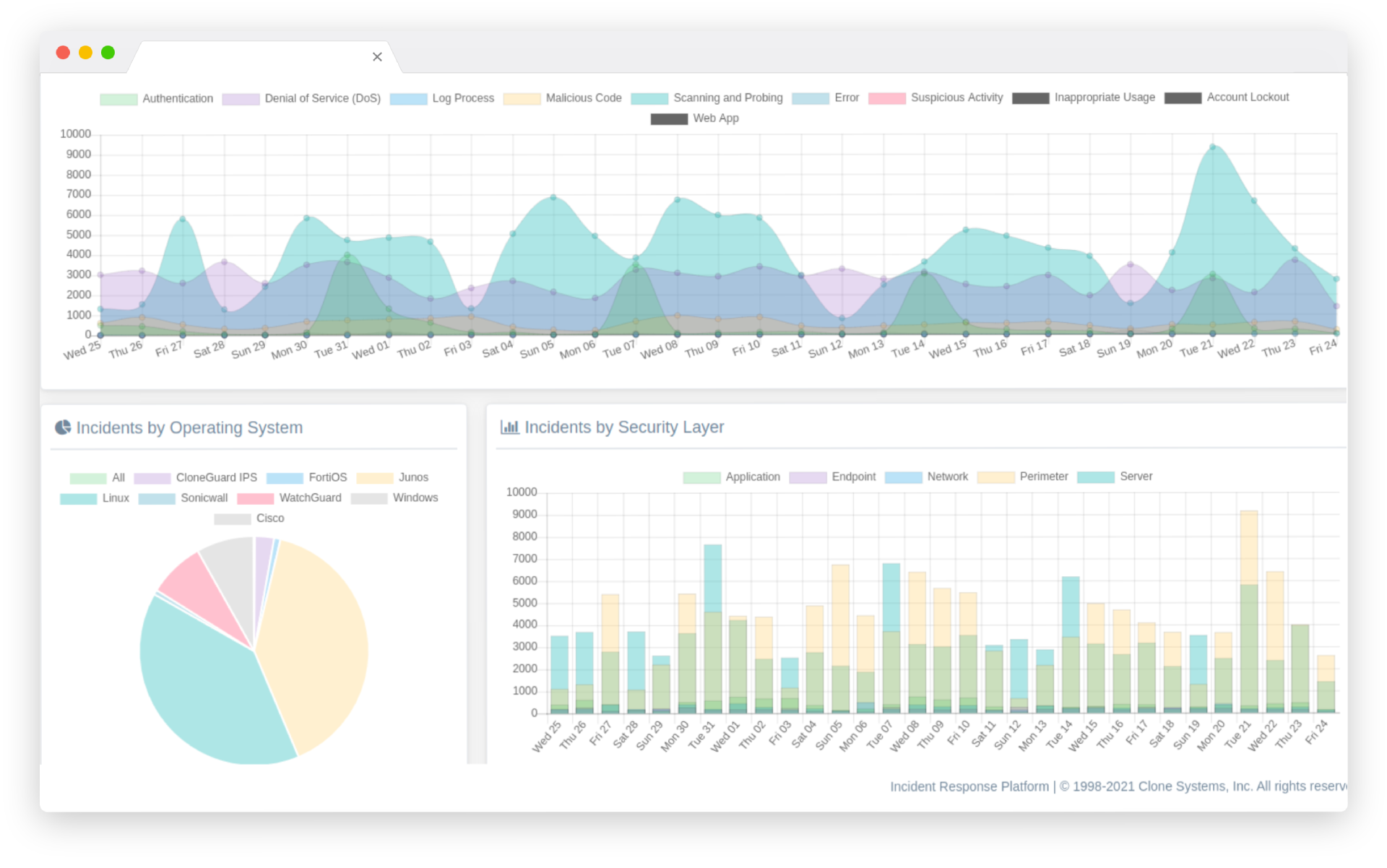
Security Orchestration is integrating a diverse ecosystem of security operations center (SOC) tools and processes to automate tasks for more efficient security operations.
Typically, security operations teams deploy dozens of Cyber Security tools to prevent, detect, and remediate threats.
However, unless these technologies and resources are fully integrated into a unified ecosystem, inefficiencies, increased security risks and decreased employee morale result.
Security orchestration addresses these issues by integrating processes and technologies to complete day-to-day SOC tasks from a single console.