Intrusion Prevention Services
Monitor your network in real-time to detect and prevent threats and vulnerability exploitation using our Intrusion Prevention Service.
Talk with our experts

Intrusion Prevention Services
Monitor your network in real-time to detect and prevent threats and vulnerability exploitation using our Intrusion Prevention Service.
Customers Around the World
prevent critical threats
Protect Your Business
Threat intelligence and signatures are consistently updated from multiple security sources. 24/7 monitoring and alerting that leverage threat intelligence to block threats and zero-day vulnerabilities. Our Security Operation Center monitors your environment and tunes the IPS to prevent critical threats.
skilled security engineers
Trust Our Experts
Vendor-agnostic expertise enables our solutions and skilled security engineers to work with any existing security infrastructure on your network. As a result, the CloneGuard® Network Security device is delivered as a fixed-cost service without requiring any capital expenditures from your budget. In addition, our security engineers maintain software updates and patches to address security infrastructure bugs and vulnerabilities.
visual THREAT representation
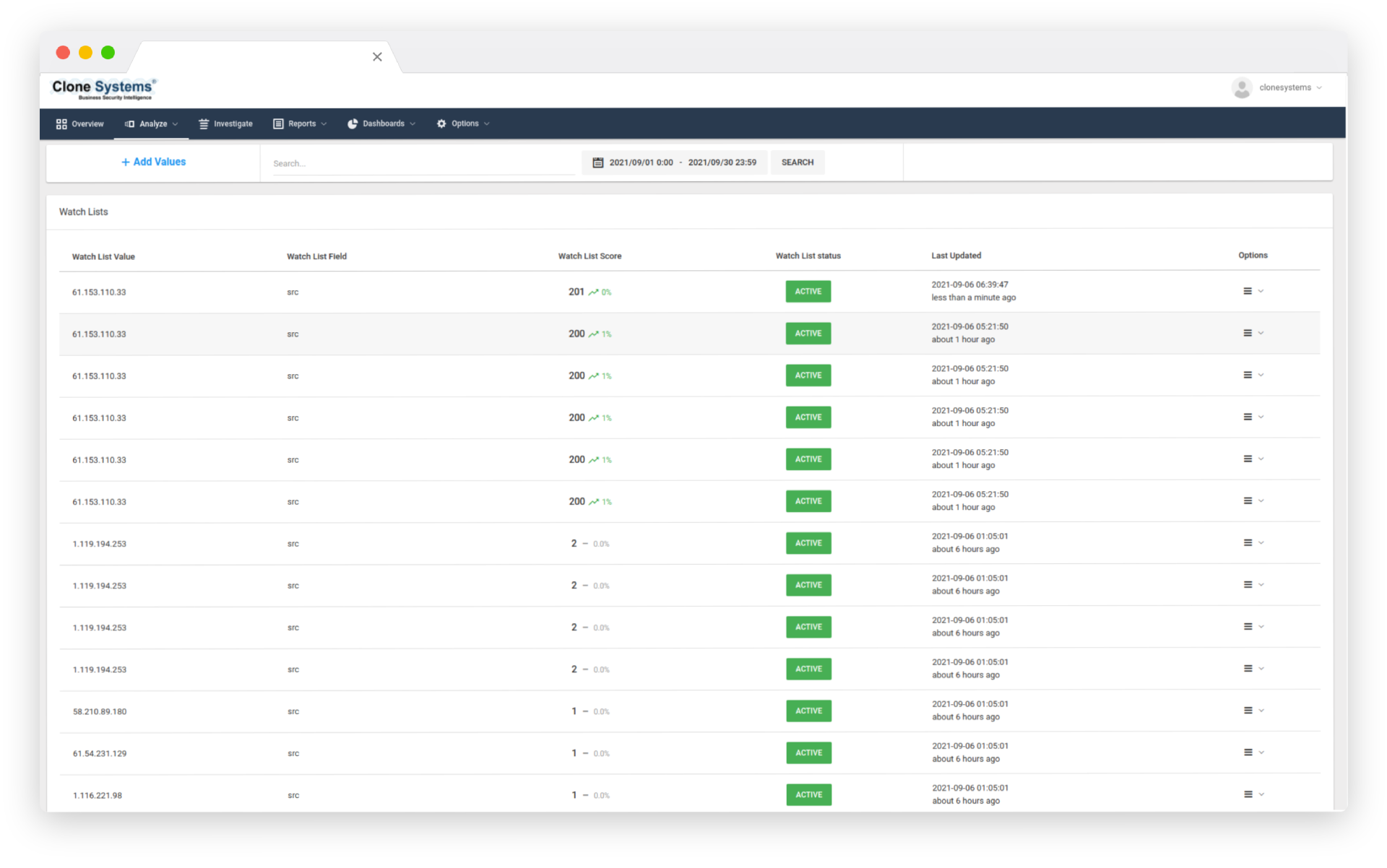
Achieve Compliance
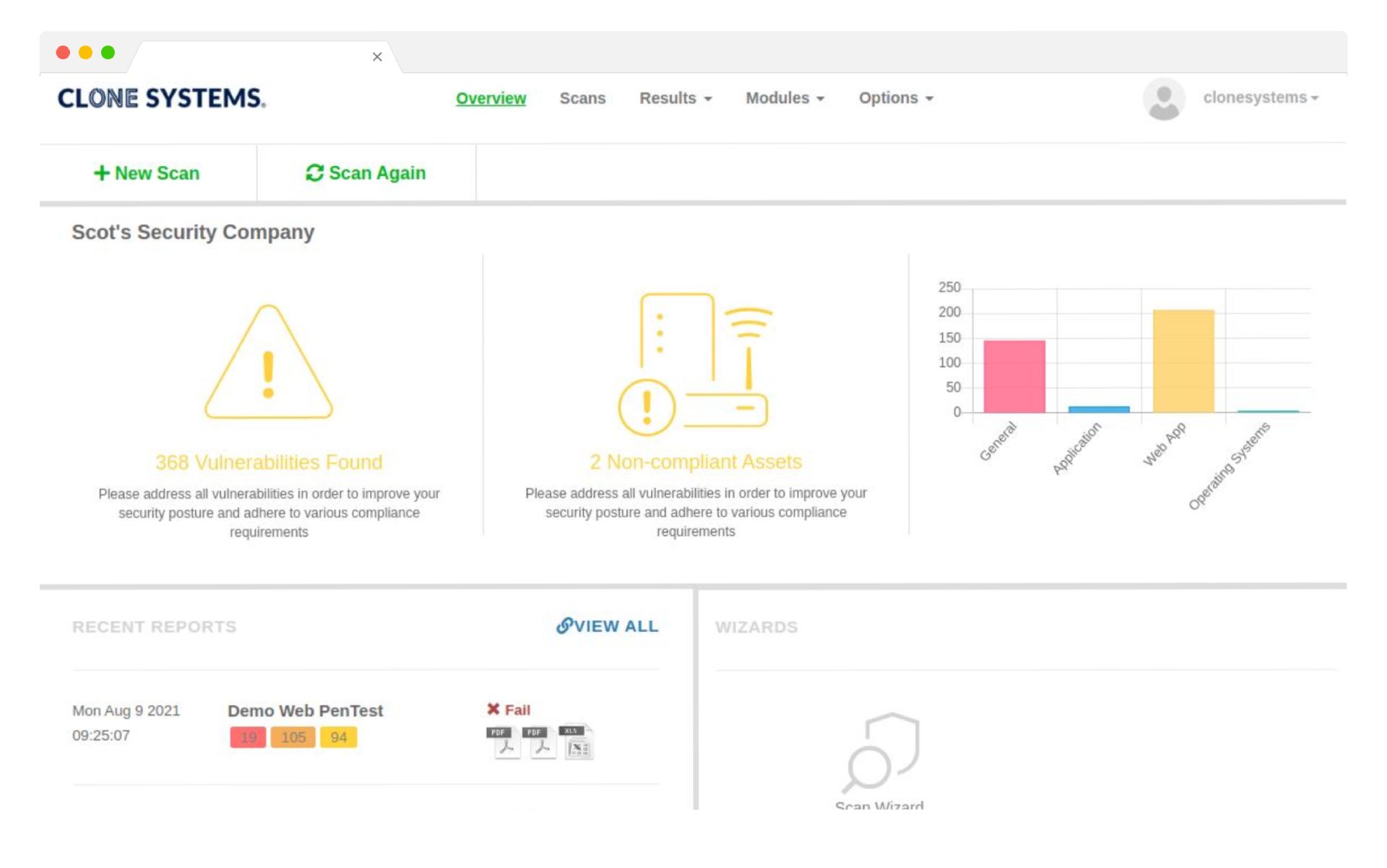
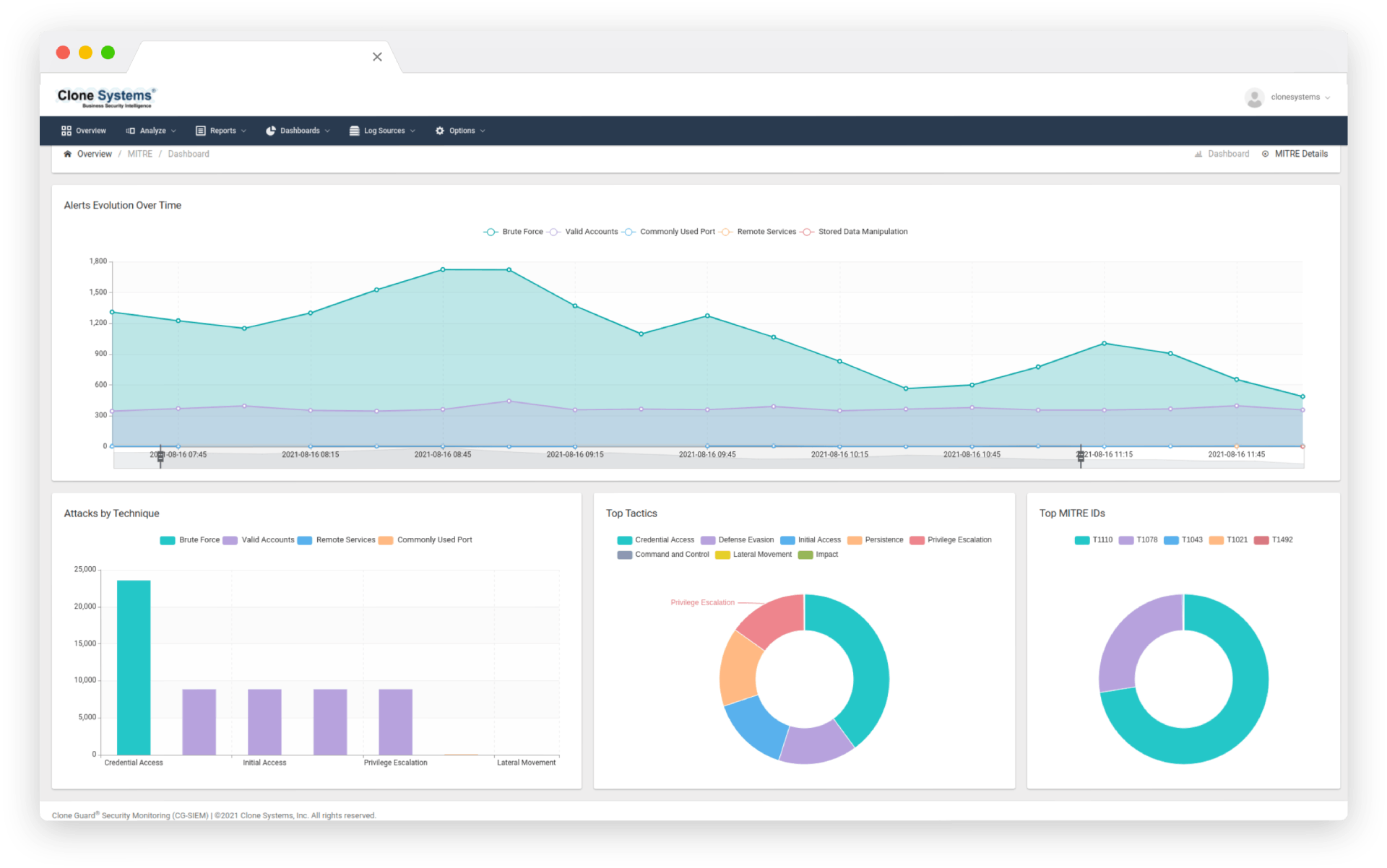
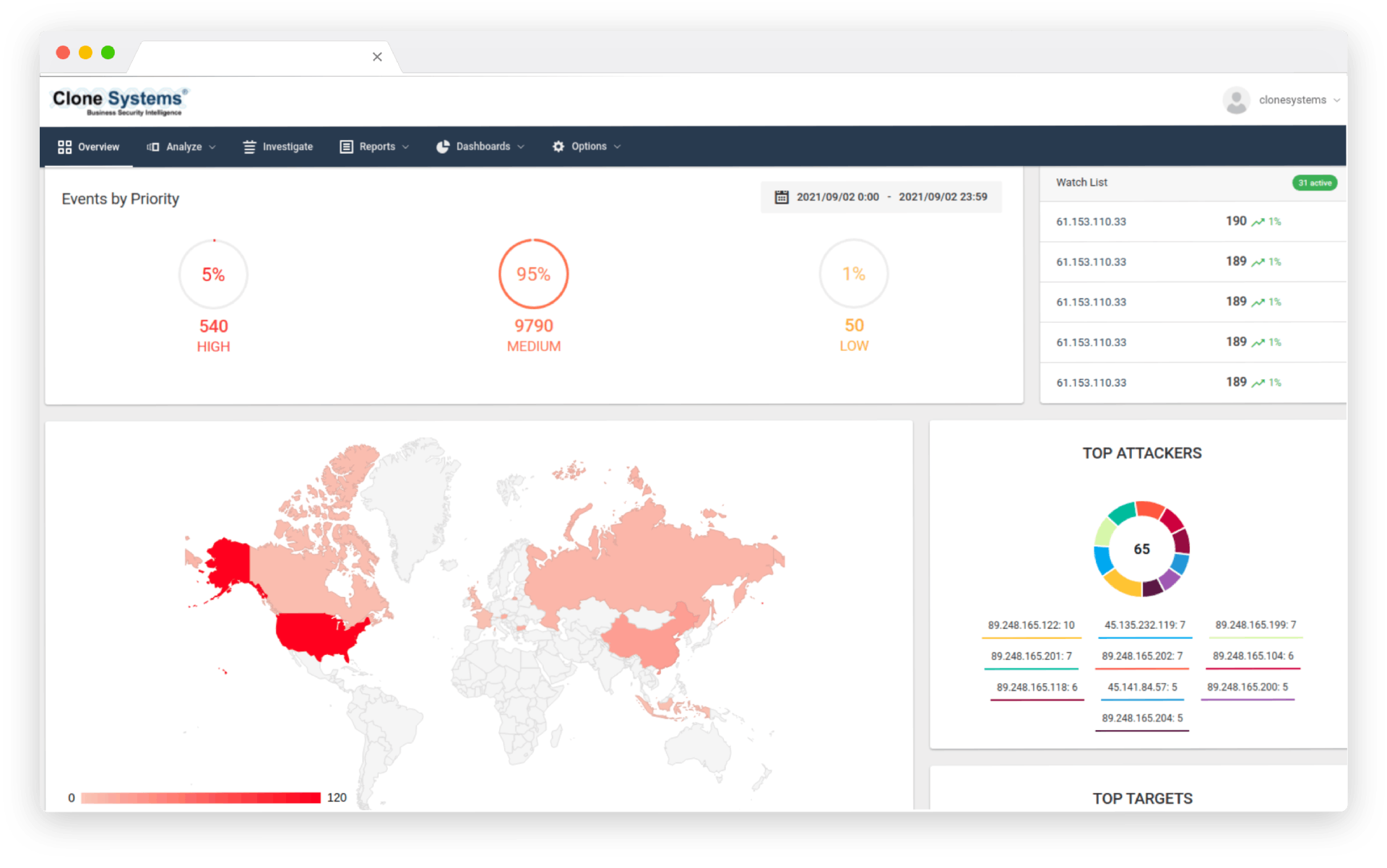
Actionable reporting tailored to your business needs, compliance standards and investigative requirements. Customizable dashboards visually represent threats and vulnerabilities, allowing you to filter detailed security event information.
*Option for Intrusion Detection Services (IDS) which allow you to monitor and detect threats
PREVENT CRITICAL THREATS
Protect Your Business
Threat intelligence and signatures are consistently updated from multiple security sources. 24/7 monitoring and alerting that leverage threat intelligence to block threats and zero-day vulnerabilities. Our Security Operation Center monitors your environment and tunes the IPS to prevent critical threats.
SKILLED SECURITY ENGINEERS
Trust Our Experts
Vendor-agnostic expertise enables our solutions and skilled security engineers to work with any existing security infrastructure on your network. As a result, the CloneGuard® Network Security device is delivered as a fixed-cost service without requiring any capital expenditures from your budget. In addition, our security engineers maintain software updates and patches to address security infrastructure bugs and vulnerabilities.
VISUAL THREAT REPRESENTATION
Achieve Compliance
Actionable reporting tailored to your business needs, compliance standards and investigative requirements. Customizable dashboards visually represent threats and vulnerabilities, allowing you to filter detailed security event information.
*Option for Intrusion Detection Services (IDS) which allow you to monitor and detect threats
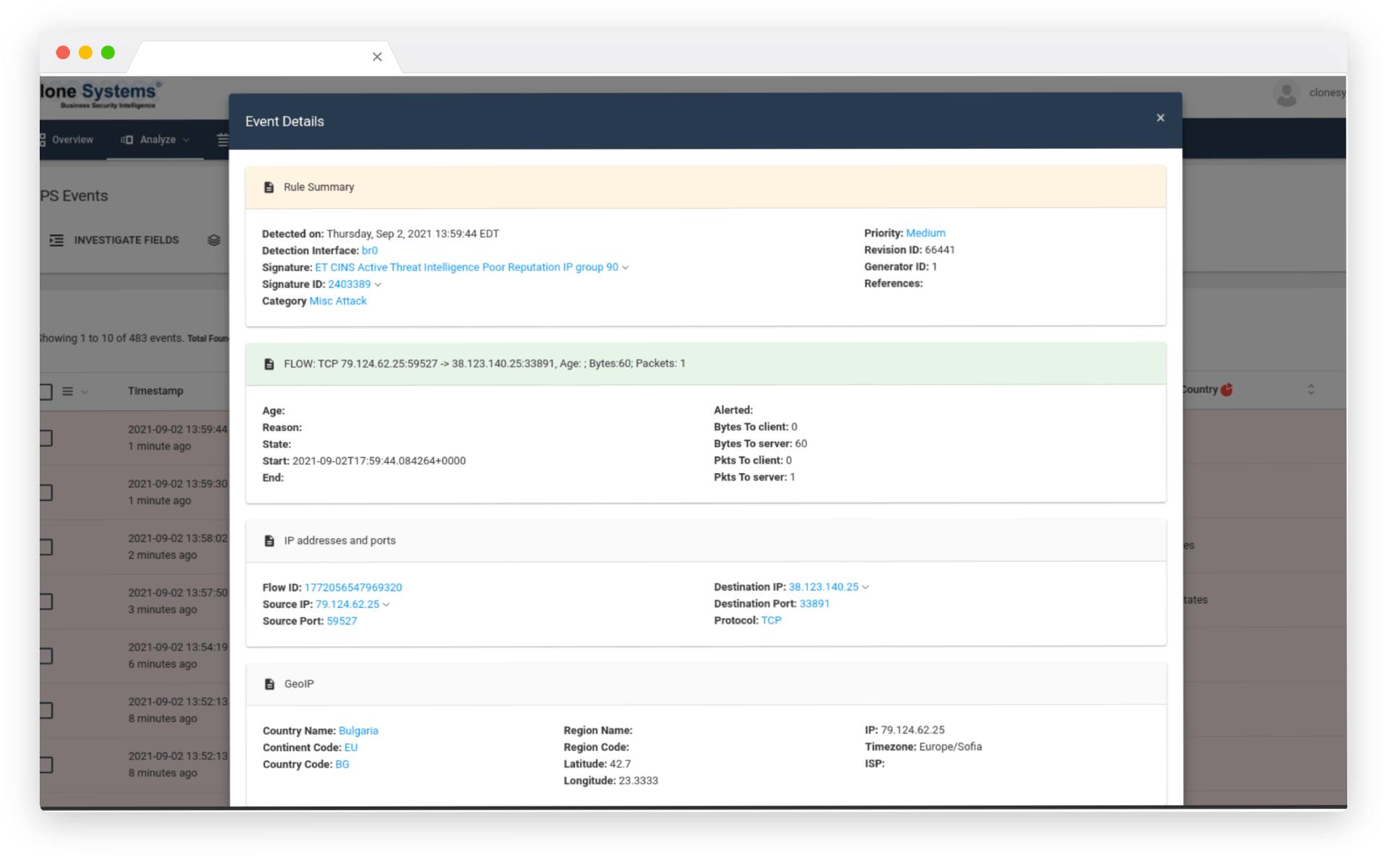
How Intrusion Prevention Services (IPS) Work
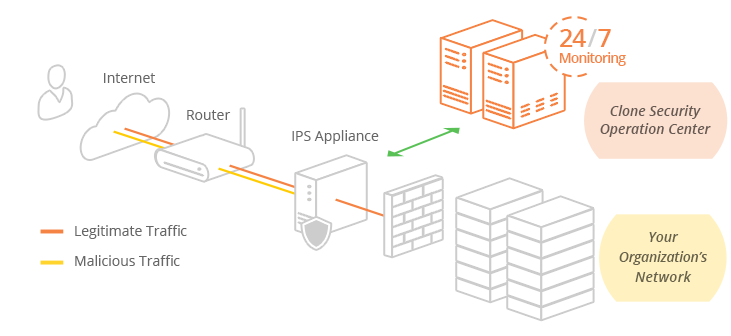
The IPS appliance is configured according to your network throughput and interface requirements. It is typically installed in-line (in-band) between your edge router and a primary firewall.
The IPS runs in protection/prevention mode and inspects all network traffic routed to your infrastructure in real-time against consistently updated threat intelligence and signature updates.
Upon finding malicious traffic such as a denial of service, brute force attack, worms, software, and network exploits, to name a few, the appliance immediately drops the packets preventing the attack from reaching its intended target.
The Clone Systems Security Operations Center (SOC) consistently monitors this activity and the appliance 24/7 to tune the IPS to distinguish critical threats from false positives and to escalate threats as needed.
Note that it is also recommended to have an IPS appliance configured internally within your network to analyze the traffic that was originally encrypted with Transport Layer Security (TLS) / Secure Sockets Layer (SSL) / Internet Protocol Security (IPsec) as this traffic cannot be inspected until it is unencrypted.
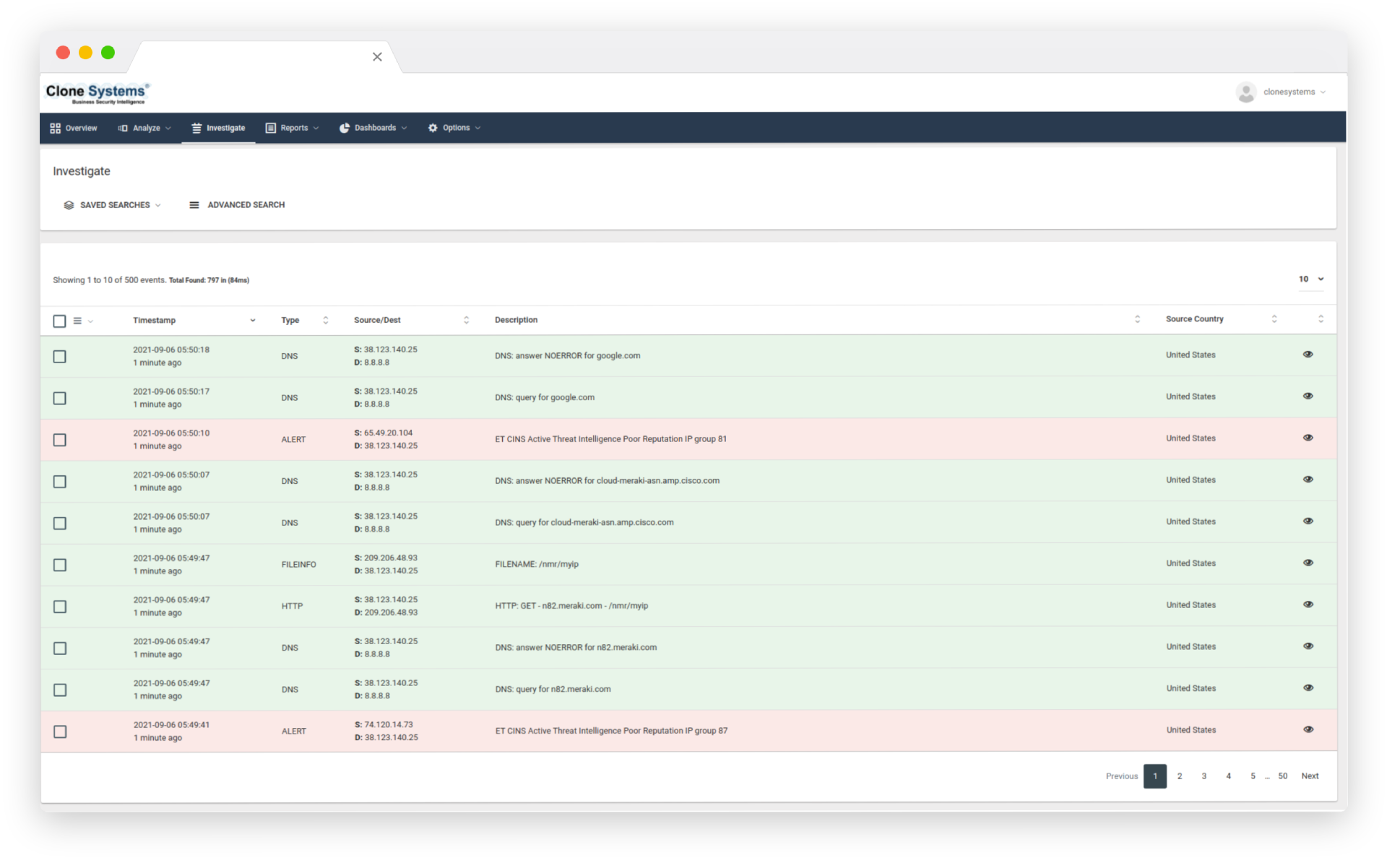
How Intrusion Detection Services (IDS) Work
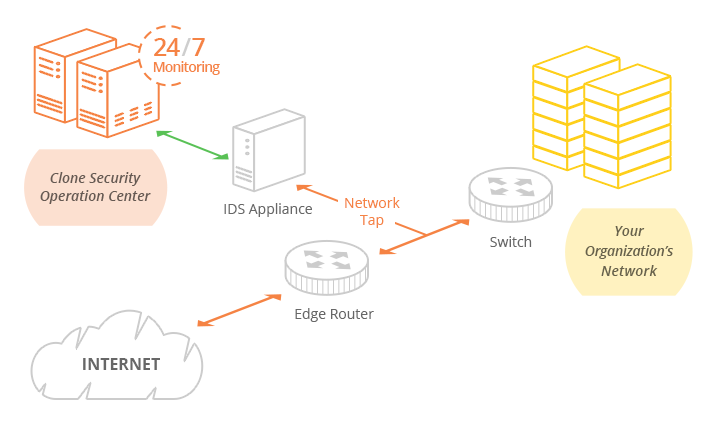
The IDS appliance is typically installed as a tap (or out-of-band). It runs in inspection/detection mode and inspects all network traffic routed to your infrastructure in real-time against consistently updated threat intelligence and signature updates.
Upon finding malicious traffic, the appliance will trigger an alert about the threat but will not try to prevent the traffic from reaching its intended target.
The Clone Systems Security Operations Center (SOC) consistently monitors this activity and the appliance 24/7 to tune the IPS to distinguish critical threats from false positives and to escalate threats as needed.
If the threat needs to be blocked, a manual step is required to drop the packets and prevent the attack from reaching its intended target.

IPS Product Sheet
Discover how you can assess your security posture with the automated Clone Guard Intrusion Prevention Services Product Sheet.